Having a phone infected with malware can be a real and prolonged nightmare, with several potential negative outcomes, from being the victim of ransomware to monetary and identity theft. There are however, several red flags to watch out for when it comes to diagnosing an infection. Knowing how to spot these warning signs will be pivotal in remedying the situation, where quick action will make all the difference. Read on for a list of red flags to be on the lookout for.
Excessive Battery and Data Drain
Pay attention to excessive, greater-than-usual battery consumption. There might be several non-malware related reasons for this, including hardware issues with the battery or camera, but it is worth looking into. High network traffic consumption is another indicator of potential infection. There is one clear criminal business model behind this: monetization through showing hidden advertisements, which require large downloads of media content not visible to the phone owner.
One option for detecting this malicious activity is to verify which processes and applications are consuming traffic. Be aware though, that some malicious code has the capability to manipulate statistics on a phone. In this case it is still possible to compare the network traffic consumption as displayed on your phone vs the telecom company’s statistics. As a consequence of monetization through hidden advertisements, the phone will often overheat and suffer from slow response-times — leading to excessive battery drain.
In some cases, limiting data usage in the background of apps can be a temporarily solution. You can also attempt to determine the malicious application by allowing and blocking access to different apps while observing fluctuations in suspicious behavior.
Random Advertisements Displayed
Another red flag is when the mobile phone shows unwanted advertisements, especially on the main screen, when the phone is unlocked or in applications that do not normally show ads. See below for an example complaint from a victim of this.
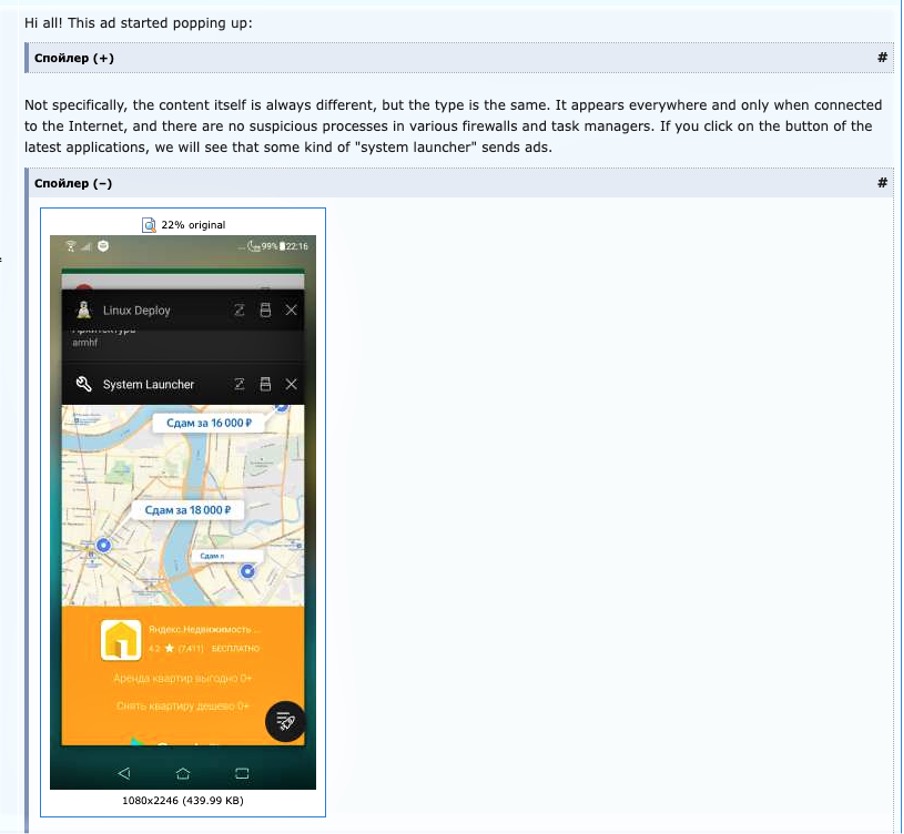
Infection of system components or malicious apps can trigger such behavior. The risks and consequences of advertisement monetization is itself not a great risk. At the same time, the fact that attackers have the capability to run a malicious code on the phone means that other attacks, including credentials and PII harvesting, can also be carried out.
Hidden Advertisements
Hidden advertisements will appear “below the surface” on a phone but be supressed from the phone owner’s point of view. As far as the advertiser is concerned, the ad is still displayed and will be paid for. Other network connected devices, such as car navigation systems, are also attractive targets for monetization though hidden adds. Since the advertisement is hidden, it can only be detected based on the side effects of advertisement processing — for example, excessive data and battery consumption.
Phone Used as a Proxy
If a mobile phone is used as a proxy, any activities (particularly criminal ones) will look like they were initiated by the phone owner. Anomalous network activity will be visible to the phone owner. In addition, excessive CAPTCHA requests while accessing legitimate sites can be an indirect indicator of potential device abuse. If your phone is monetized as a proxy in this way, other people — criminals mostly — will be surfing the internet off the back of your resources.
Mobile proxies are high-demand tactics among cyber-criminals. They are often used in scenarios like credential stuffing, credit card fraud, and abuse of promotional campaigns. When it comes to criminal investigations of related proxy activities, owners of infected devices can easily become suspects themselves for law enforcement agencies.
Browser Opens New Tabs Without User Interaction
If your phone takes unexpected actions without your input, this is always suspicious behavior. One major red flag is when the phone opens a browser or browser tab unilaterally. Often the tabs will be pop-up ads or malicious webpages, and indicates someone has access to your phone’s system.
Phone Installs Apps Without Owner Consent
The appearance of new applications without the user’s request can be triggered by malware. Malicious applications installed on infected phones can be used for different types of monetization, for example, promoting an application (increasing number of downloads). In the other cases, criminal business models can use this tactic for credential harvesting and monetization of your PII. The impact of such installations varies, but the capability to remotely install and execute apps on the victim’s phone indicates serious risk.
Phone Downloads Files That User Hasn’t Requested
As well as applications, malicious files can also be downloaded by an infected phone. The appearance of said unexpected files is a major red flag. In this case, the user will see notifications related to file downloads, or a new file download folder. Some malicious files are almost impossible to remove by the user themself. An example discussion of such symptoms is shown below.
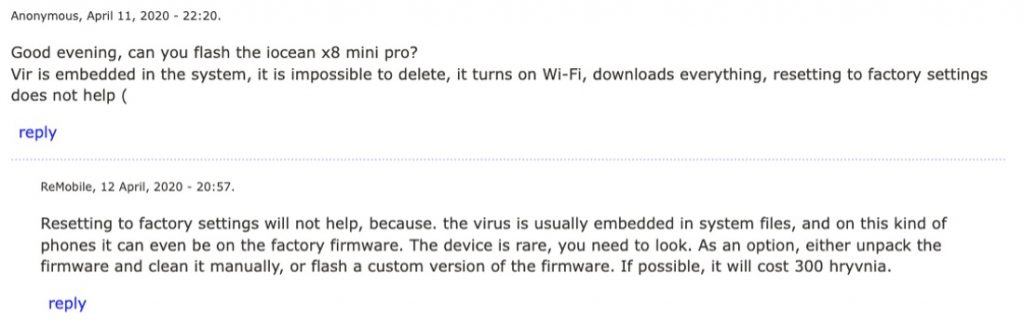
The appearance of such behavior can lead to a variety of serious risks, but is highly dependent on the type of malware and monetization strategy used by the attacker.
Unexpected Phone Number Usage
Unexpected SMS messages with requests to click links, or calls from “the bank” to confirm fictitious transactions, both indicate phishing attempts. Another red flag is unexpected confirmations of your phone number being registered to a service. Both can be a symptom of a malware infection. Being billed for calls abroad is another giveaway. Likewise, if your phone number has already been used to register for a service you want to acquire. To protect against these risks, be sure to regularly keep tabs on your phone balance.
The key security risks and potential consequences in this situation are related to digital identity theft. Attackers will be capable of operating accounts through different services, which will be linked to the victim’s digital identity; this can be messaging accounts used to trick people into transferring money, or something more sophisticated.
In addition to this, on a phone compromised in this way, the victim’s connected social media accounts could then be hijacked and used to distribute spam to their contacts. Similarly, an attacker can use the infected phone to receive and then sell on SMS messages (see our article on SMS PVA for reference).
Paid Subscriptions Without User Consent
Our final red flag pointing to malware infection is the appearance of paid subscriptions without any act or consent from the phone owner. The appearance of unwanted subscriptions can mean that the required steps were carried out by malicious code embedded in the phone. Since SMS confirmation is usually required to initiate such subscriptions, it is likely that the malicious code on the phone has SMS interception and suppression capabilities — a serious security risk. Those same capabilities can also be used to take over a variety of accounts linked to the phone, leading to criminal acts such as the redirection of payments.
Trend Micro Has Your Back
Knowing what to look out for can make all the difference when it comes to malware-infected phones. Using this list of red flags, you’ll be able to respond timely to better protect and prevent your phone from falling into the hands of cybercriminals.
In the meantime, users should consider our popular Mobile Security app, available on Android and iOS and with a FREE download option available today.
Mobile Security uses an advanced AI scan and Web Guard feature to protect you against malicious apps, ransomware, dangerous websites, unsafe Wi-Fi networks, unwanted access to your device, and more. It will also optimize your mobile phone to keep it running at peak performance.
As always, we hope this article has been an interesting and/or useful read. If so, please do SHARE it with family and friends to help keep the online community secure and informed. Be safe out there, folks — and consider leaving a like or comment below.
