HTML pages that have been incorporated into phishing emails are regularly used by cybercriminals. They do so because it negates the necessity of including links in the body of the email, which antivirus software and antispam technologies can usually detect with ease. When compared to email, HTML offers more options for information concealment.
In phishing emails, HTML files are routinely used to redirect visitors to dangerous websites, download files, or even display phishing forms locally within the browser. Email security software routinely overlooks attachments because HTML is not inherently dangerous, allowing them to successfully enter would-be victims’ inboxes.
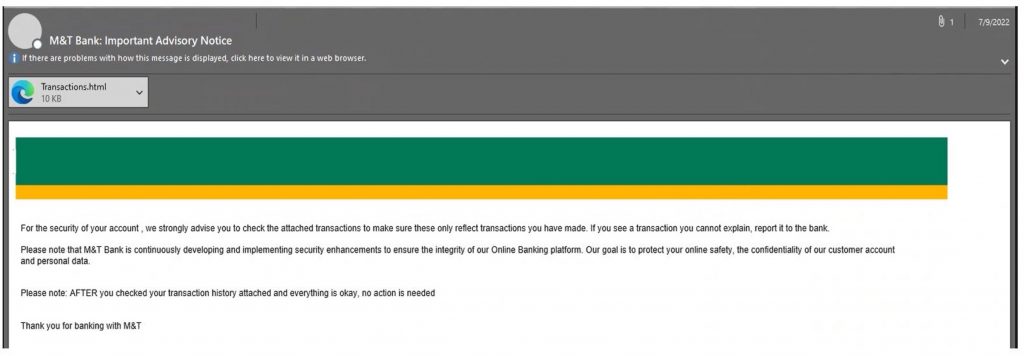
How Does an HTML Attachment Attack Work?
Instead of using links to direct victims to a fake cloud or bank log-in page, hackers are now enticing users into downloading a fake log-in page. When a person downloads and opens an HTML attachment in the browser, the webpage is hosted on their device rather than the internet, necessitating the need for a public URL.
Without a URL pointing to it, a phishing page has no reputation. The hacker finds this advantageous since it frees them from having to maintain a phishing page on a compromised site, and helps them to get around the rigorous HTML constraints placed on email bodies.
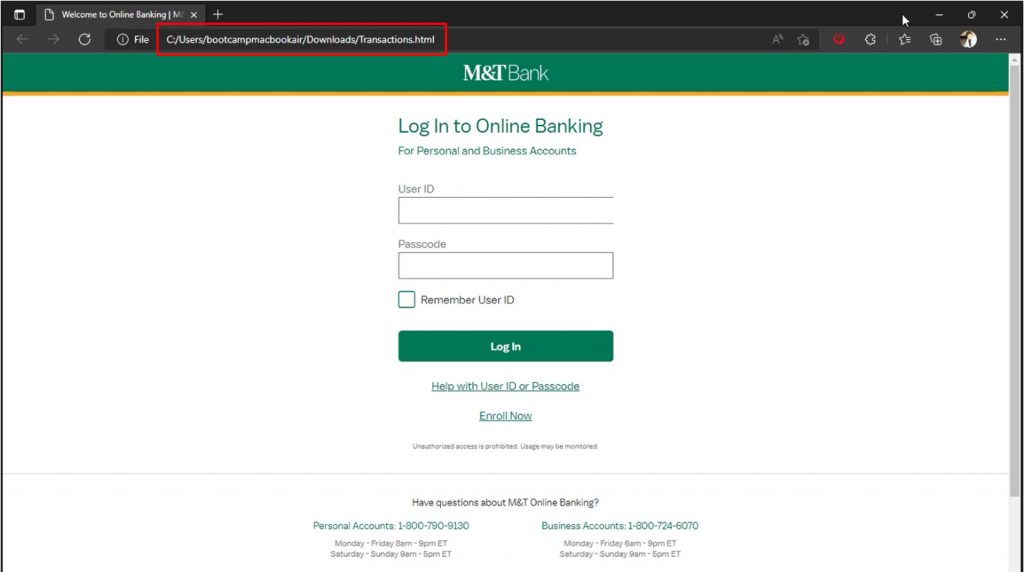
You will be redirected to a fake log-in page after opening the locally saved HTML attachment. Notice the address bar doesn’t contain a URL but rather the location where the HTML was saved.
How to Protect Yourself
Although the distribution of HTML attachments in phishing emails has been around for a while, it is a tactic many still fall for today. Follow these steps to avoid joining the victims:
- HTML attachments must always be viewed with extreme suspicion. Never open it without first carefully examining what it is.
- Unfortunately, Windows disables the showing of file extensions by default, which frequently prevents extensions from being noticed. To avoid the opening of harmful files it is advised to enable the viewing of file extensions.
- Beware of suspicious email addresses — especially ones sent from email providers such as Gmail or Outlook.
- Never click on links or attachments from unknown sources. Use Trend Micro ScamCheck to surf the web safely (it’s FREE!).
- Add an extra layer of protection to your devices with Trend Micro Maximum Security. Its Web Threat Protection, Ransomware Protection, Anti-phishing, and Anti-spam Protection can help you combat scams and cyberattacks. Click the button below to give it a try:
