A newly discovered Android malware was found to be capable of collecting tons of personally identifiable information (PII) from infected devices – including banking credentials.
Dubbed SOVA (after the Russian word for owl) and discovered by the cybersecurity firm ThreatFabric, this banking malware has tons of credential-stealing features. The malicious software is capable of keystroke logging, hiding notifications, performing web overlay attacks, and modifying cryptocurrency wallet addresses on users’ devices. The developers of the malware have posted online about their future plans to enable SOVA to commit on-device fraud, perform DDOS attacks, deploy ransomware, and even intercept two-factor authentication codes. If they are successful in doing so, SOVA will easily be the most powerful mobile malware ever.
Researchers from ThreatFabric also pointed out that SOVA is capable of performing one highly uncommon banking-trojan feature rarely seen in Android malware – the ability to steal session cookies. This allows the malware to piggyback on valid logged-in banking sessions, meaning it doesn’t need to have a victim’s banking credentials to access their account.
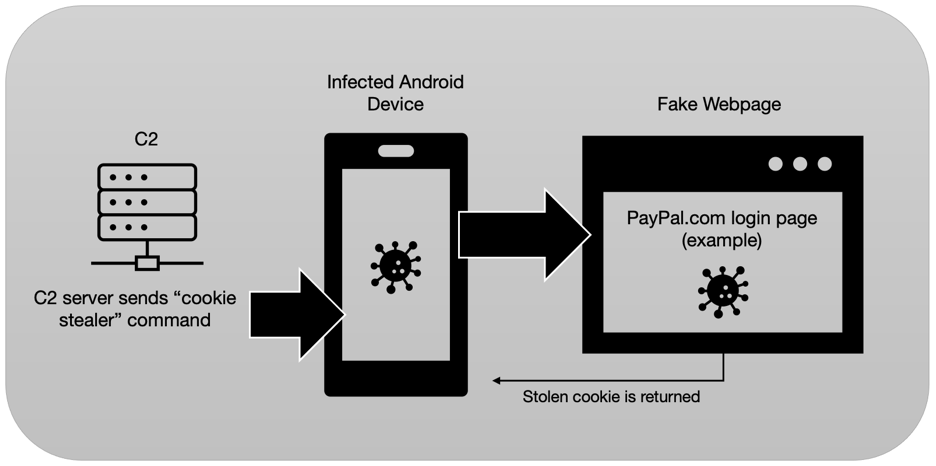
“Cookies are a vital part of web functionality, which allow users to maintain open sessions on their browsers without having to re-input their credentials repeatedly” the ThreatFabric researchers explained.
SOVA can hijack a user’s browser session, replace a legitimate site with a fake version, and steal their browser’s cookies after they log in. This allows the malicious software to easily steal session cookies from web apps and sites like Gmail and PayPal.
The authors of the SOVA banking Trojan have been seen advertising the product on underground hacking forums since July, which was when they started looking for people to test their malicious code.
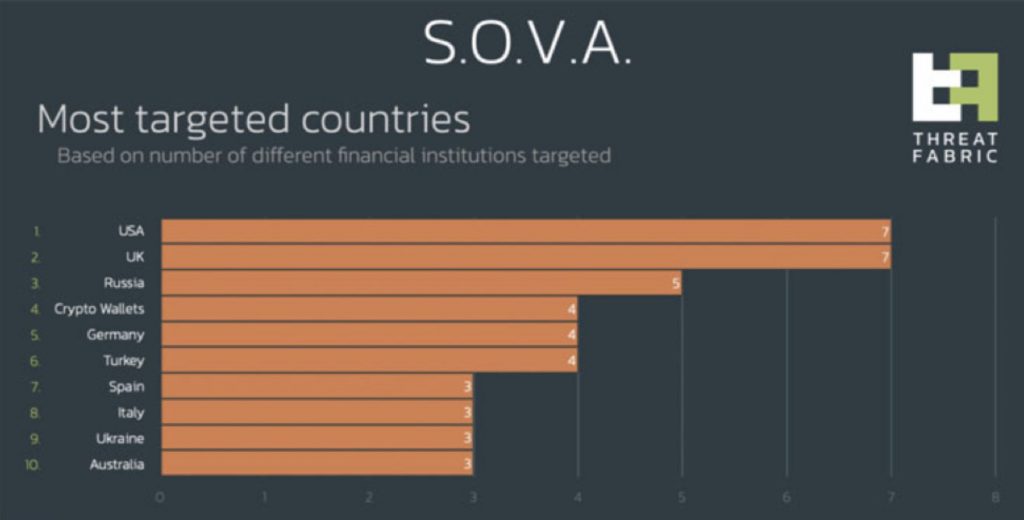
Financial institutions across the world have been targeted, but the data shared by ThreatFabric shows that the most attacked countries were the US, the UK, and Russia.
How can I protect my device against SOVA?
Trend Micro Mobile Security (TMMS) offers comprehensive anti-malware capabilities via its real-time Security Scan feature. Security Scan alerts you to any malware hidden in apps before they can be installed on your device.
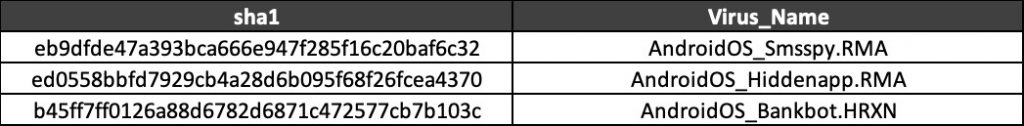
Currently, Trend Micro Mobile Security can detect the following samples of the SOVA Android malware:
Trend Micro Mobile Security can also detect when SOVA is attempting to trick you into thinking you’re using a real website or app – protecting your login information from being stolen.
