For many hackers around the globe, ransomware infections have become a lucrative business. Although these types of malware samples have been around for years now, they continue to spur success – and high monetary profits – for attackers.
In fact, according to a statement from U.S. Deputy Attorney General Rod Rosenstein during the 2017 Cambridge Cyber Summit, ransomware attacks now impact over 100,000 endpoints on a daily basis. The severity of these infections and the frequency at which victims pay up on ransom demands has enabled attackers to rake in nearly $1 billion in successful payments, Government Technology reported.
However, not every attack is the same, and even in cases when victims pay hackers’ demands, access to data is not always returned.
To pay or not to pay?
When a ransomware notification appears on-screen, there are numerous questions and considerations that immediately jump to mind. How will the organization support daily operations? How will users access important files and data? Are there backups in place that the business can fall back on?
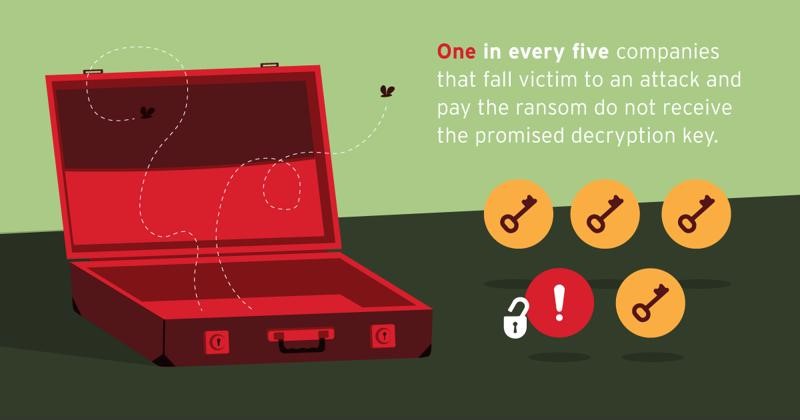
One of the top questions, though, is whether or not to pay the ransom.
In 2016, the FBI, which is keeping a close eye on the spread and severity of ransomware infections, noted that victims shouldn’t give in to demands and should not pay attackers’ ransoms, Forbes reported. As demonstrated by Kaspersky Labs’ data, this advice is sound, as approximately one in every five companies that fall victim to an attack and pay the ransom do not receive the promised decryption key.
In other words, businesses are out money and are not returned access to their critical applications, files and data.
“Unfortunately, however, as is the case with most ransomware attacks, the stakes of losing years worth of important data is always quite high and the ransom demanded usually very small, leading most victims to give in to the attacker’s demands before even reaching out to law enforcement,” explained Forbes contributor Harold Stark.
Let’s examine a few real-world ransomware infection cases, and what can happen when victims do decide to pay attackers.
Indiana hospital pays $55,000 after SamSam infection
According to ZDNet, an Indiana-based hospital, Hancock Health, elected to pay $55,000, or the equivalent value of 4 Bitcoin at the time, after its systems were seized by ransomware sample SamSam. Despite immediate awareness and notification by employee end users, the hospital’s IT team wasn’t able to stem the spread of the pervasive ransomware sample.
All told, the infection impacted nearly all of the hospital’s key IT systems, and users were locked out of email, the electronic health record system and other internal platforms. This includes more than 1,400 files, which were encrypted by attackers and renamed as “I’m sorry.”
The sample used in this case, SamSam, seeks out vulnerable servers, and is able to spread to other machines within the network, enabling a quick and widely-scoped attack. And as ZDNet contributor Charlie Osborne pointed out, hackers will make decisions about the ransom amount based on how far SamSam spreads within the victim’s infrastructure.
“Known for use in targeted rather than opportunistic attacks, SamSam can be used in web shell deployment, batch script usage for running the malware on multiple machines, remote access and tunneling,” Osborne explained.
After the initial infection and ransom demand, hospital administrators were given a week to pay the ransom or risk losing their files and data forever. Although the organization did have backups in place – a key data security best practice – it elected to pay the ransom. IT administrators at the hospital explained that while the backups could have been leveraged to recover data and files decrypted by hackers, this process would have taken days, or even weeks. What’s more, after shifting certain work activity to a manual, pen-and-paper basis for two days, the hospital simply needed a quick resolution.
Unfortunately, the hospital is far from the only organization to be infected with the pervasive SamSam sample – in the spring of 2018, Trend Micro reported on a case involving the city of Atlanta. During that attack, the city’s local services, including citizen-facing platforms used to pay bills or access court data, were made unavailable. In this instance, hackers demanded $6,800 to decrypt a single computer or $51,000 for a full decryption. City officials worked with their internal IT team and Microsoft to restore access.
Kansas hospital hit with second infection after paying ransom
While the Indiana hospital infected by SamSam was able to regain its files and data after paying hackers’ ransom, not every organization is so lucky.
According to HealthcareITNews contributor Bill Siwicki, Kansas Heart Hospital in Wichita was the victim of a ransomware attack in mid-2016. While patient data contained within the hospital’s electronic health records system was not impacted and daily operations were able to continue, officials decided to pay the ransom.
Unlike the Hancock Health case, though, access to files and data was not returned, even after the “small amount” in ransom was sent to attackers. Instead, hackers demanded a second ransom and systems impacted by the initial infection remained locked.
“Kansas Heart Hospital did not pay the second ransom request and said that along with consultants it did not think that would be a wise move, even though attackers still appear to have some of their data locked,” Siwicki wrote.
This hospital’s experience isn’t as unique as it might seem, though. Health care security expert Ryan Witt told Siwicki that hackers will often take part in a “tried and tested dance” wherein they demand a small ransom amount, and then demand a second, higher amount once the first is paid.
“Demands for funds are soaring, and the problem is organizations are paying,” Witt noted. “Ransomware will get worse before it gets better.”
Addressing ransomware: Trend Micro’s File Decryptor
As these cases have shown, paying up in the hopes that a ransomware attack will end is not the best strategy. It’s imperative that organizations have backups of all of their critical files and data, and that these are stored in the cloud or another separate, off-site location. In this way, should an attack take place, IT admins can recover using the company’s backups.
In addition, Trend Micro has established a solution specifically to address the issue of ransomware attacks: the Trend Micro Ransomware File Decryptor. This tool works to decrypt and restore files and data impacted by certain ransomware families. As of May 2017, limited decryption support was added for WannaCry, following the widespread impact of the sample.
0 Comments
Other Topics
