Have you heard about the recent incident involving Colonial Pipeline and JBS? Ransomware has gotten a lot of attention over the last few weeks, and with good reason. Do you want to know more? Let’s get started.
What is Ransomware?
Ransomware restricts access to your computer or encrypts your files, holding them ransom until you pay a fee to the malicious actors who have them hostage. But, paying the ransom doesn’t guarantee they will unlock your computer or decrypt your files and give them back. Instead, they can leave you hanging and take away your money.
Ransomware Cases
Trend Micro’s Threat Research was able to identify the top three ransomware that targeted consumers from January 2021 to April 2021.
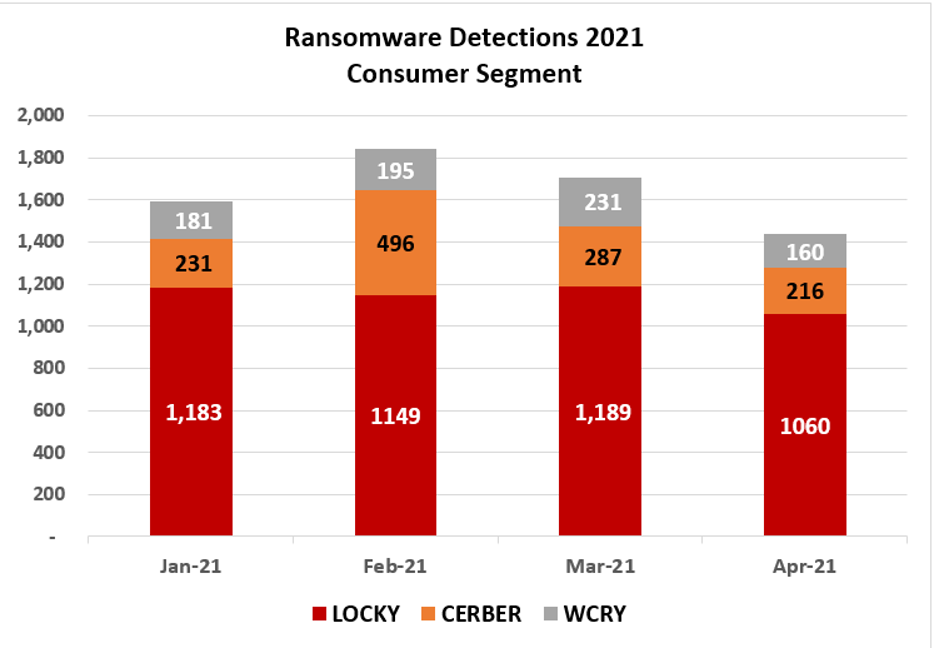
Locky: Infiltrates systems via email with a Word document containing malicious macros.
Cerber: Arrives on your system as a dropped file by another malware or files downloaded and run unwittingly by people accessing malvertisements or malicious websites.
Wcry: It infects the PC using a file dropper that takes advantage of the vulnerability in legacy versions of Windows.
Also, ransomware has been preying on large corporations over the last few weeks. Cyber attacks on companies such as Colonial Pipeline and JBS have real-world ramifications for all of us.
Colonial Pipeline:
- While the pipeline’s operational technology systems were unharmed, a shutdown was necessary to protect the company from further threats due to the compromised billing system.
- Fuel shortages occurred at filling stations as panicked fuel consumers rushed to buy their fill. Some gas stations ran out of fuel as average fuel prices increased.
- The shortage led to rerouted flights, additional refueling stops, or plane swaps for a couple of days. Also, other fuel providers had to be used to deal with the deficit.
JBS
- The attack disrupted all JBS USA facilities, including those focused on pork and poultry. Thus, all JBS-owned beef facilities in the United States were temporarily shut down for the time being.
- The attack disrupted the beef sector in Australia. As a result, JBS “downsized” 7,000 Australian employees in June.
- Since the attack, the USDA could not release wholesale prices for beef and pork that agricultural markets depend on daily.
The bottom line is even if the ransomware attack targeted a large company, its effects trickle down to the consumers.
How Can I Get Infected with Ransomware?
We now know the most prevalent ransomware attacking consumers over the past few months. Moreover, we’ve also seen how ransomware may leave a significant impact on our lives; thus, we should be mindful that the infection does not begin with us.
There are various ways that ransomware can infect your computer.
- Visiting malicious or suspicious websites may have downloaded the ransomware unintentionally.
- Some ransomware comes as attachments to a spammed email.
- Using outdated and unpatched software, operating system, or device exposes your computer system to vulnerabilities that ransomware can exploit to spread itself on the system.
- Other entry modes include social engineering that lures unwitting users to download malicious software from a compromised website.
- Clicking on “malvertising” fake ads is another means by which it can get on your computer.
- Likewise, it can enter your system through malicious links in chat or email messages.
- Using borrowed-and-possiblyinfected removable USB drives becomes an entry point as well.
- In some cases, it arrives as a payload that another malware has either dropped or downloaded on your device.
Tips to Protect Yourself from Ransomware
- Double-check the source of every email. The email should only be taken seriously when you have confirmed it was issued by the bank. If the message was sent by your contact, double-check its authenticity. You shouldn’t trust exclusively based on personal ties, as a friend or family member could also be victims of spammers.
- Check message content for glaring inconsistencies. Check your claims with your bank or friend to ensure they are valid. Social engineering can be used to fool recipients into opening a message.
- Avoid clicking links in emails, chats, and social networking platforms.
- Keep your software and computer updates current. Up-to-date software gives another layer of defense against various attacks.
- Having an up-to-date backup of your files is good practice. Follow the 3-2-1 rule: three copies, two different media, and one different location.
- Only download from reputable websites or sources.
How Can Trend Micro Protect Me from Ransomware?
As the saying goes, the best defense is a good offense. You can prevent ransomware from infecting your system with Trend Micro Maximum Security and Antivirus for Mac.
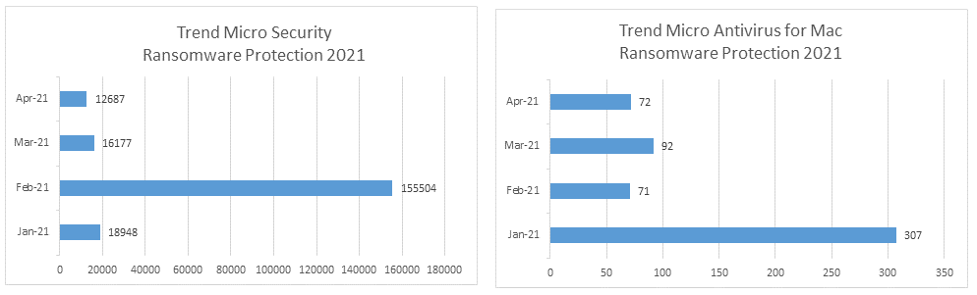
As seen from the graph, Trend Micro successfully detected and blocked ransomware from both Windows and Mac. Although, there’s a few ransomware in Mac, the data set shown proves that Mac is not impervious to ransomware attacks.
Trend Micro Security and Antivirus for Mac can protect you from ransomware through its comprehensive set of security capabilities:
- Uses machine learning to protect from new or unknown threats
- Prevents programs on portable drives from launching automatically (Windows only)
- Immediately closes programs that have been exploited by hackers (Windows only)
- Protects documents against unauthorized encryption or modification (Windows only)
- Backs up files encrypted or modified possibly due to malware activity (Windows only)
- Folder Shield limits access to files within the protected folders in multiple user accounts, preventing ransomware from maliciously encrypting your files
- Identifies and blocks malicious links in websites, social networks, emails, and instant messaging
- Trend Micro Toolbar enabled for Safari, Google Chrome, or Mozilla Firefox proactively warns you about any security risks associated with links on websites you visit
- Email Defender protects your Outlook.com and Gmail webmail from scams and phishing attacks that may lead to ransomware infection
Ransomware isn’t going anywhere, so don’t let cybercriminals hold your computer and data hostage. Use a robust security solution like Maximum Security and Antivirus for Mac to defend you against ransomware attacks.
