Trend Micro has identified more malicious Android apps abusing the name of the popular mobile game Super Mario Run. We earlier reported about how fake apps were using the app’s popularity to spread; attackers have now released versions of these fake apps that steal the user’s credit card information.
Super Mario Run is a mobile game that Nintendo first released on the iOS platform in September 2016, followed by the Android version on March 23, 2017. Mobile games have always proven to be attractive lures for cybercriminals to get users to download their malicious apps and potentially unwanted apps (PUAs). This is not the first time that the name of a popular game was abused; we’ve discussed how the popularity of Pokémon Go was similarly abused.
Based on feedback from the Smart Protection Network™, we saw more than 400 of these apps in the first three months in 2017 alone. In the same time frame, we saw 34 fake apps explicitly named “Super Mario Run”—it’s a noteworthy trend, as we saw the first of these only in December 2016.
In this post we’ll discuss the behavior of a new credit card stealing variant named “Fobus” (detected as ANDROIDOS_FOBUS.OPSF).
Fobus was distributed via third-party app stores. As is the norm, it asks for various permissions:
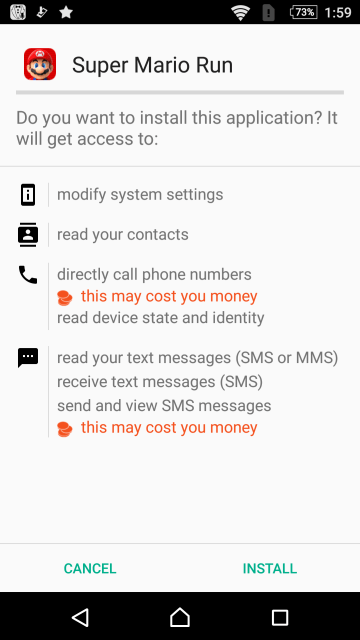
During the installation process, it also asks for itself to be activated as a device administrator:
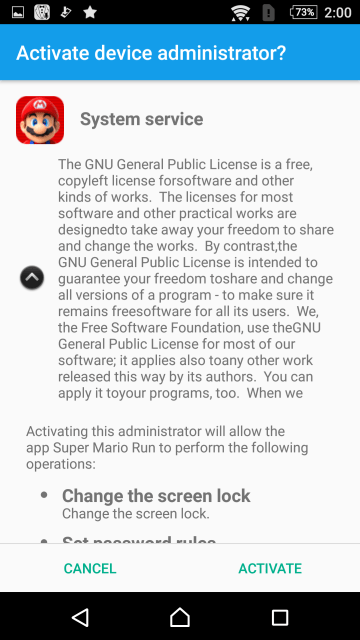
After it is successfully installed, it gathers sensitive information such as the user’s mobile number, contact information, location, and SMS messages from the device. The device administrator privileges allow it to hide its own icon if the user tries to run the fake app, which has the same icon as the real Super Mario Run app. This also makes uninstalling the fake app more difficult. No version of the game is actually installed.
The real purpose of this app is to steal credit card information. When Google Play is launched with this app installed, a fake screen pops up and asks the user to enter their credit card information. Even if user tries to click on the grayed out area in the background, the pop-up cannot be closed; the user has no choice but to access Google Play by providing credit card information into the field.
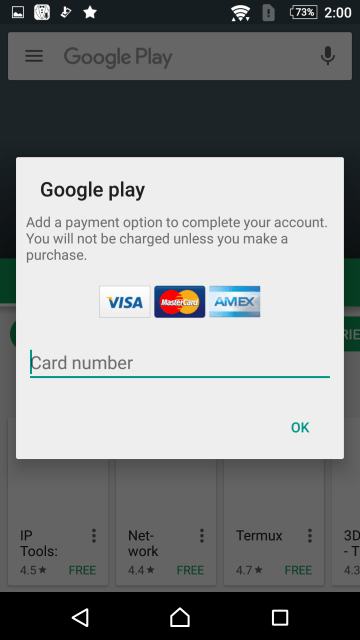
The app goes as far as to check if the entered card number is a valid one. The first six digits identifies the issuing network of the card (i.e., Visa, Mastercard, etc.), and the app displays the logo of the appropriate network. It also uses the Luhn algorithm to check if the number is valid. If an invalid number is entered, it displays an error message saying “Incorrect credit card number”.
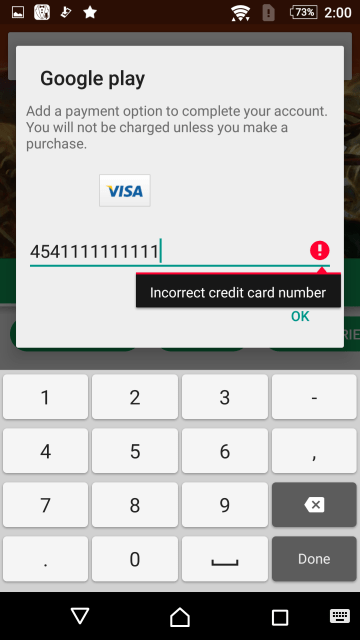
If a valid card number is entered, the app then displays additional fields asking for the card holder’s name, the card’s expiration date, and security code—information that is located on the card itself.
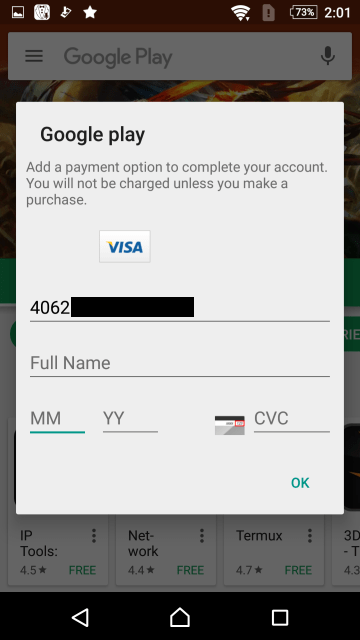
When the user completes this information, it will ask for even more information, this time related to the user: the user’s birthday, address, and phone number. After entering all the information, the user can finally access Google Play.
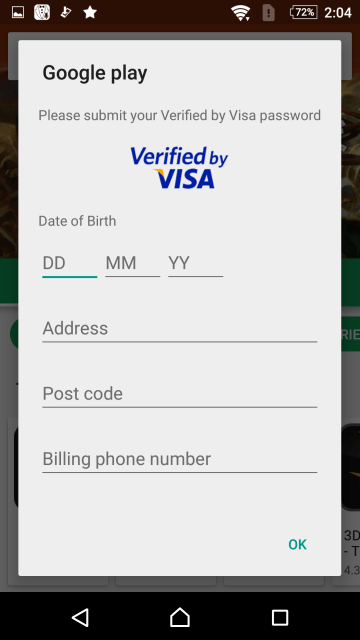
The app also allowed a remote attacker to reset the device’s PIN; this was done via commands issued by a command-and-control (C&C) server. This allowed an attacker to lock the user out of their own device. This C&C server also receives the credit card information stolen from the user in the previous steps.
Mitigation
Cybercriminals frequently take advantage of popular and hotly anticipated titles to push their own malicious apps. These are usually distributed via third-party app stores. Some users may utilize such app stores to download “unreleased” versions of legitimate apps, or to obtain apps for free. These apps are illegitimate in the first place, and the risks to end users are quite high. We strongly advise that users download and install apps only from legitimate app stores such as Google Play or trusted third-party app store.
In other cases, an attacker may even provide a fake app store that resembles Google Play. Alternately, a message supposedly from a friend sent via social media may lead to a malicious app. Disabling the “Allow installation of apps from unknown sources” setting prevents apps inadvertently downloaded these ways from being installed. By default, this setting is set to off. Only turn it on if you know you are installing an app from a trusted third-party app store.
To carry out malicious behavior such as installing other apps on the user’s device without any user input and consent, or hiding icons and processes, an app needs device administrator privileges. Legitimate apps seldom require these; users should double check whenever an app asks for them. This is particularly true of games, which do not require device administrator privileges. A “game” asking for these privileges is likely to be malicious or a PUA.
Trend Micro solutions
Users should only install apps from the Google Play or trusted third-party app stores and use mobile security solutions such as Trend Micro Mobile Security to block threats from app stores before they can be installed and cause damage your device or data.
Enterprise users should consider a solution like Trend Micro™ Mobile Security for Enterprise. This includes device management, data protection, application management, compliance management, configuration provisioning, and other features so employers can balance privacy and security with the flexibility and added productivity of BYOD programs.
