Smishing combines “SMS” and “phishing” to describe a type of phishing scam conducted through SMS (Short Message Service) texts. Scammers send texts that appear to be from legitimate sources, such as financial institutions or government bodies, to trick individuals into divulging personal information, clicking on dangerous links, or calling a fraudulent phone number. As a result, victims of smishing can face significant financial losses, such as unauthorized charges on their accounts or complete depletion of their bank balances. Additionally, identity theft, a common consequence of smishing, can lead to broader issues including legal complications, damage to credit scores, and long-term harm to one’s personal reputation.
Keep on reading to learn everything you need to know about smishing and how to stay safe.
How Does Smishing Work?
Smishing attacks often involve scammers sending text messages to many phone numbers, hoping to reach as many potential victims as possible. By casting a wide net, scammers increase their chances of deceiving individuals who may not be vigilant about the authenticity of the messages they receive.
Smishing messages are designed to mimic communications from trusted sources, such as banks, government agencies, or well-known brands. Would-be victims are often urged to click on links that lead to malicious websites, provide sensitive personal information, or contact a fraudulent phone number. Following the instructions in a smishing text can potentially result in identity theft, financial losses, and other serious consequences.
Common Smishing Scams
Smishing scams can come in a near infinite number of varieties. However, they all have one thing in common: they’re looking to trick you into compromising your privacy or security. Below are a few examples:
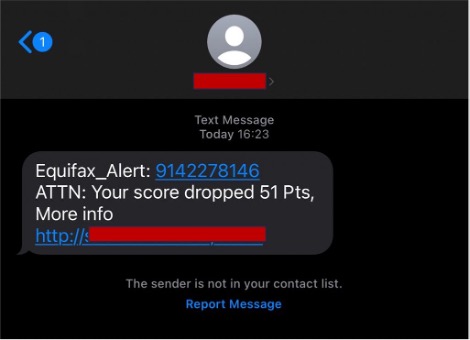
Credit Score Dropped Scam
This scam attempts to get you to click on a link that leads to a dangerous website by claiming your credit score has dropped.
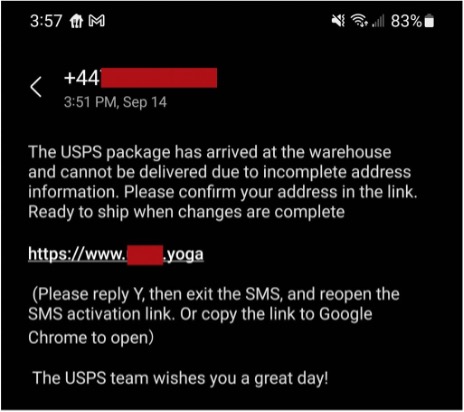
Failed Delivery Scam
By impersonating a trusted delivery company, this scam attempts to trick you into entering your personal information on a scammer-controlled website. If you were to do as instructed, your personal information would be immediately shared with the scammers.
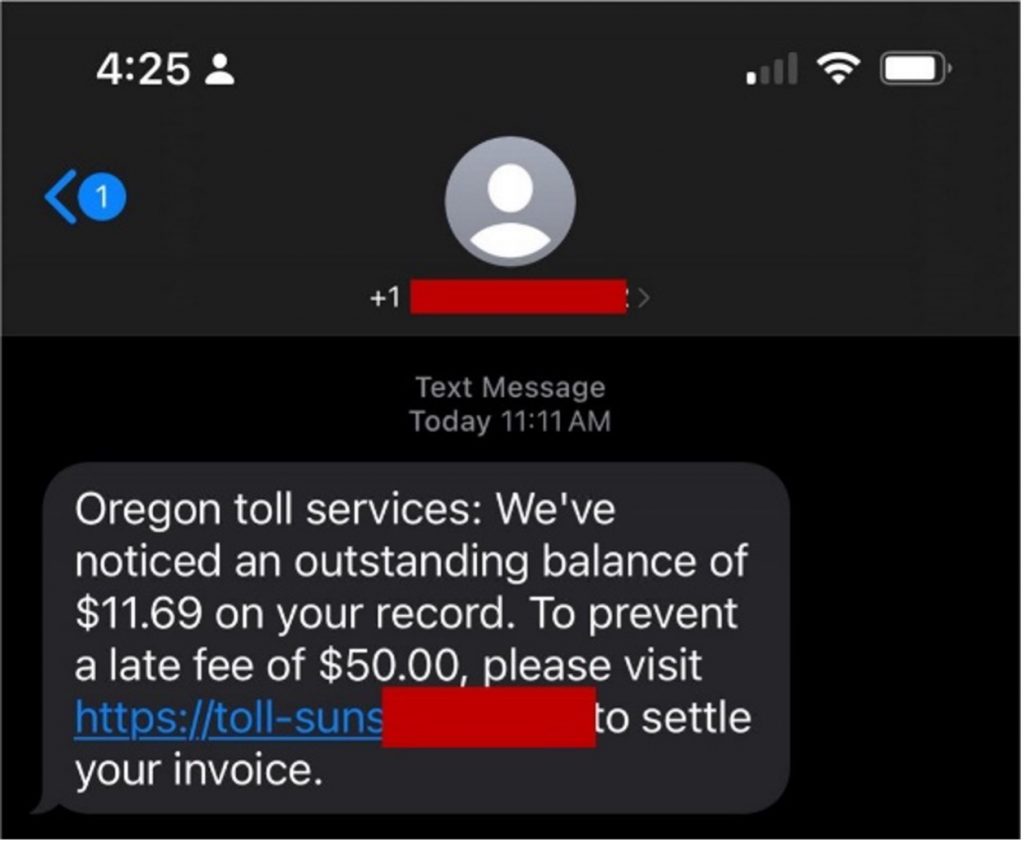
Unpaid Toll Scam
This scam has been very popular recently. Claiming that you have unpaid tolls, the scammers urge you to visit a website to pay them and avoid the late fee. Any personal or financial information entered on the website will be immediately accessible by the scammers.
What Information Do Scammers Want?
Scammers are opportunistic and will take whatever information they can get their hands on. However, certain types of data are particularly valuable to them because they can be used to commit more extensive fraud or sold on the dark web. Here are some of the key types of information that smishing scams often target:
- Personal Identification Information:
- Examples: This includes sensitive details like your full name, date of birth, Social Security number, driver’s license number, and passport details. Such information can open the door to various fraudulent activities under your name.
- Financial Information:
- Examples: Data such as credit card numbers, bank account details, PINs, and other banking credentials are prime targets. This information can directly enable financial theft.
- Login Credentials:
- Examples: Usernames and passwords for online accounts, including email, social media, and work-related systems are highly sought after. These credentials can give attackers access to a wealth of personal and potentially sensitive information.
- Contact Information:
- Examples: Information like phone numbers, email addresses, and home addresses may seem less sensitive but can be used for targeted follow-up scams.
- Health Information:
- Examples: Details such as health insurance numbers, medical records, and prescription information are highly valuable for committing medical or insurance fraud.
How to Protect Yourself from Smishing
Here are some essential tips to help you avoid falling victim to smishing:
- Be Skeptical of Unsolicited Messages: Always treat unsolicited texts with suspicion, especially those that ask for personal or financial information or claim there will be consequences for not acting quickly.
- Avoid Clicking on Links: Do not click on links in text messages unless you are absolutely sure they are from a trusted source. Even then, it’s safer to access the service directly through its official website or app.
- Verify the Source: If a message claims to be from a legitimate institution and demands urgent action, verify its authenticity by contacting the institution directly using a phone number or email address from its official website.
- Use ScamCheck: The newly updated ScamCheck can automatically filter spam and scam text messages, keeping you safe from smishing scams. Check below for more information about Trend Micro ScamCheck.
Protect Yourself Against Smishing with ScamCheck
With the increasing number and sophistication of smishing scams, staying one step ahead is more crucial than ever. Unfortunately, antivirus software alone isn’t enough. Introducing the newly updated Trend Micro ScamCheck! Available for both Android and iOS, Trend Micro ScamCheck offers comprehensive protection from deceptive smishing scams, scam and spam text messages, deepfakes, and more:
- Scam Check: Instantly analyze emails, texts, URLs, screenshots, and phone numbers with our AI-powered scam detection technology. Stay secure and scam-free.
- SMS Filter & Call Block: Say goodbye to unwanted spam and scam calls and messages. Minimize daily disruptions and reinforce your defenses against phishing.
- Deepfake Scan: Detect deepfakes in real-time during video calls, alerting you if anyone is using AI face-swapping technology to alter their appearance.
- Web Guard: Surf the web safely, protected from malicious websites and annoying ads.
To download Trend Micro ScamCheck or to learn more, click the button below.
If you’ve found this article an interesting or helpful read, please SHARE it with friends and family. Also, please consider clicking the LIKE button below.
