Malware Posed As a Google Chrome Update Error Message
Google Chrome users who use the browser regularly should be wary of a new attack campaign that distributes malware by posing as a Google Chrome update error message. The attack campaign has been operational since February 2023 and has a large impact area.
How Might I Be Affected?
The attack starts when you visit a legitimate, albeit compromised, website that has been infected with a malicious code, including code relating to adult sites, blogs, news sites, and online stores.
When you visit these websites, a fake Google Chrome error message will prompt you to download an update to fix a supposed security issue. What you’re really downloading is a ZIP file that has an EXE file inside. This EXE file contains a Monero miner that will use your computer’s processing power to mine cryptocurrency for the attackers.
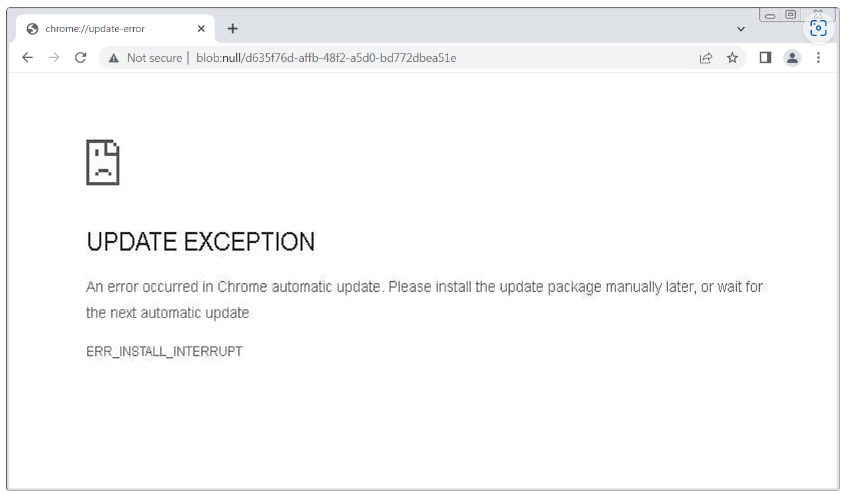
What Is the Risk?
If you become infected with the malware:
- Your computer may slow down and become unresponsive due to the Monero mining process consuming system resources.
- The downloaded malware has the potential to acquire sensitive information such as log-in credentials and financial data from the your computer.
- Your device will be vulnerable to further attacks because the malware is capable of modifying system settings, including disabling or interfering with security solutions.
Tips to Protect Yourself
To avoid falling victim to this attack, you should:
1. Always exercise caution when downloading anything from unknown sources, and limit software downloads to only trusted websites.
2. Keep in mind that keeping your operating system and software up-to-date is a good security practice, including your web browser.
For Google Chrome users, use the built-in update feature by clicking Help and selecting About Chrome.
3. It’s important to stay informed about the latest threats and best practices for protecting yourself so that you can take proactive steps to safeguard yourself and your personal data from cyberattacks.
4. Safeguard your computer against malware by installing antivirus software such as Trend Micro Maximum Security. Its powerful features can help detect and remove threats before they cause damage.
What Is Cross-Site Scripting?
Users should also be aware of cross-site scripting (XSS) attacks. Contrary to popular belief, attackers do not need to directly access a website to inject a malicious code: search bars, comment sections, and even contact forms, can be vulnerable to attacks.
In this way, attackers can inject their own code and compromise the website’s security. For example, an attacker could enter malicious code into a website’s comment section, and when other users view the comment, the code will be executed in their web browser.
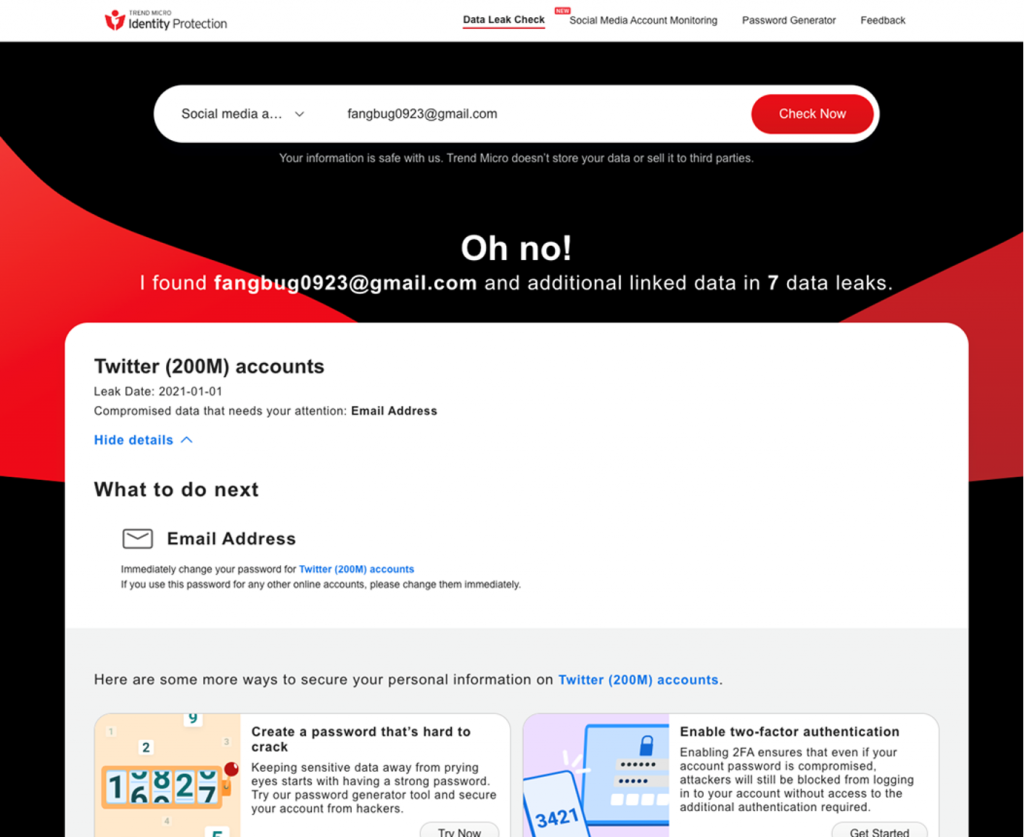
Protecting Your Identity and Personal Info
Compromised log-in credentials can have serious consequences, including identity theft and financial fraud. The best thing you can do is a) have reliable cybersecurity protection, and b) ensure you will find out ASAP in the event of being affected. We would encourage readers to head over to our new FREE ID Protection platform, which has been designed to meet these challenges.
![IDP_LilyColins__Fake ChatGPT App[64]](https://news.trendmicro.com/api/wp-content/uploads/2023/03/IDP_LilyColins__Fake-ChatGPT-App64-1024x563.jpg)
With ID Protection, you can:
- Check to see if your data (email, number, password, social media) has been exposed in a leak,
- Secure your social media accounts with our Social Media Account Monitoring tool, with which you’ll receive a personal report,
- Receive the strongest tough-to-hack password suggestions from our advanced AI.
All this for free — give it a go today. As always, we hope this article has been an interesting and/or useful read. If so, please do SHARE it with family and friends to help keep the online community secure and informed — and consider leaving a like or comment below. Here’s to a secure 2023!
