The hackers behind Flubot are not short of creativity, that’s for sure. The latest update to the banking Trojan added a fake security warning designed to trick potential victims into thinking their devices have been infected with, you guessed it, Flubot!
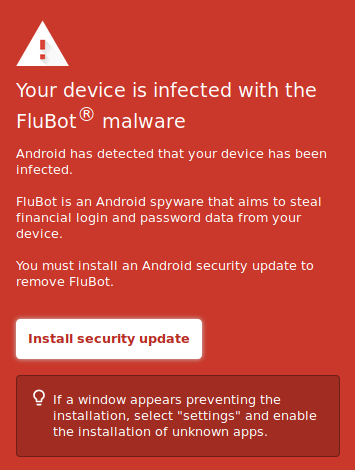
The new fake warning message replaces Flubot’s old installation page. The alarmingly convincing message attempts to entice people into clicking on the “Install security update” button. At which point their devices will become infected with Flubot — for real this time!
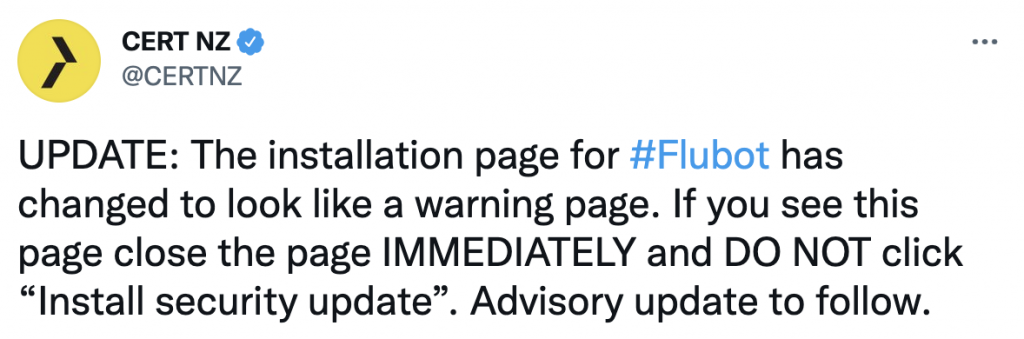
New Zealand’s Computer Emergency Response Team (CERT NZ) posted a Tweet warning people of the update to the Trojan after it was discovered.
Thousands of Android users in Australia have recently been targeted by Flubot — a destructive malware that is spreading through scam text messages.
It was only back in April that Flubot was wreaking havoc across Europe. Originally spotted in Spain, it wasn’t long before the malware began spreading quickly throughout the UK, Germany, Hungary, Italy, and Poland.
Australians have been taking to social media in droves to express their frustrations at being bombarded by the scam messages:
What is Flubot and how does it work?
Flubot is a particularly devastating mobile malware. It targets Android users by sending them SMS messages that say they have a new voicemail message. Oftentimes, the messages appear to come from well-known delivery or telecommunications companies.
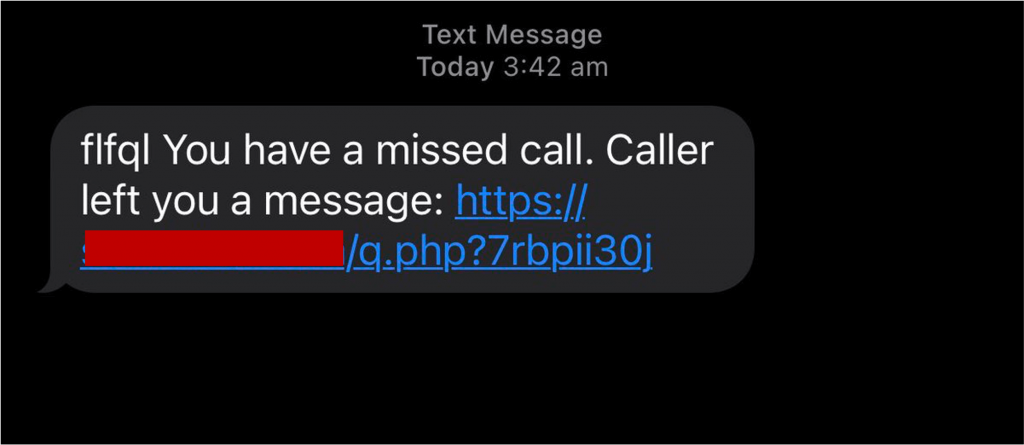
To listen to the voicemail message, the victim needs to click on the included link and download an app. If the scammers are impersonating a well-known company, the link will take the victim to a fake version of the company’s website, and the malicious app they’re prompted to download will appear to be from the company, too. Otherwise, as in the example below, the victim will be asked to download a fairly generic-looking voicemail app.
Regardless of which variant of the scam the victim is subjected to, if they install the app, their phone will become infected with the Flubot malware. If the victim grants the app the permissions it asks for, the malware will be free to access anything stored on the phone, including credit card and personal information. Flubot can also send and intercept SMS messages, open web browser pages, and trick people into entering additional personal information such as passwords.
Because Flubot is free to read any information stored on a victim’s phone, the scammers can access their contacts, gaining all the information they need to target many more people.
You need to protect yourself
For the victims of Flubot, the fallout could be immense. When scammers have access to all the personal information stored on your phone, they can use it to empty your bank account, log into all your online accounts, and even steal your identity.
The best defense is a good offense
To be sure you come out on top in the fight against Flubot you need two things – good mobile hygiene and an excellent mobile antivirus app. Here are some top tips:
- Keep your device’s operating system updated, use strong, unique passwords, and enable multi-factor authentication.
- In Settings on your Android device, disable “Install Unknown Apps”. This makes it so you can only install apps available from the Google Play Store, and not from unknown sources. If you do this, Flubot won’t be able to make it onto your device.
- Never open links in suspicious messages. Make sure you know who sent you the message before you click on anything.
- Be careful when granting apps broad permissions. You should only give apps access to the data they need to function, nothing more.
- Immensely strengthen your device’s security by using a mobile antivirus app. Trend Micro Mobile Security is guaranteed to stop Flubot dead in its tracks. The app detects and blocks Flubot — and other cybersecurity threats — before they can even be installed, ensuring complete protection.
Accidentally installed Flubot? Here’s what to do
To properly remove the malware-infected app, you need to uninstall it in safe mode. Here’s how to do it:
1. Press and hold the power button.
2. Tap and hold Power off.
3. When the Safe mode icon appears, tap it.
4. Find the Flubot app on your phone, tap and hold the app, and drag it to the trash can icon to uninstall it.
To turn off Safe mode:
1. Press and hold the power button.
2. Tap the Restart icon.
Once you’ve uninstalled the malicious app, run a scan using Trend Micro Mobile Security to be sure your device is 100% safe and secure.
