Malware (a portmanteau coined from the words “malicious” and “software”) is a collective term for any piece of software, script, or code designed to perform specific behaviors that have undesirable results for the affected users of a computer system or network. These undesirable results include anything from annoying pop-up ads or messages, disruption of normal computer operations, to the exposure of personal or confidential data. In this article, we will introduce 10 common types of malware, instruct you how to detect and remove malware infection on your PC, and share 8 tips to avoid it with our anti-malware protection:
Common types of malware?
Different types of malware are categorized based on how they work and spread. Here are the most common ones:
 Viruses
Viruses
Viruses are able to infect normal files by inserting malicious code. They can replicate and spread throughout an entire system.
 Trojans
Trojans
Trojans are executable programs that do not replicate but instead reside on computers and perform malicious acts, such as opening ports for hackers to enter through.
 Spyware
Spyware
Spyware is programs that monitor and gather user information for different purposes. They usually run in the background, with their activities invisible to most users.
 Worms
Worms
A worm is malware that is designed to propagate and spread across networks.
Worms do not infect files but may carry one or more payloads, often with the goal of compromising computer security or committing information theft.
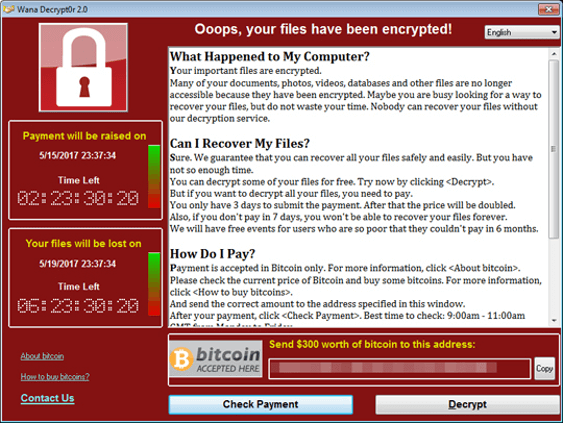
 Ransomware
Ransomware
Ransomware is a type of malware that encrypts files and demands a ransom to be paid in order to decrypt or unlock the infected machine.
 Adware
Adware
Adware, or “advertising-supported software”, refers to any piece of software or application that displays advertisements, usually through pop-ups or pop-under windows. While they may be disruptive to some users, they are not inherently malicious and are actually considered grayware.
 Scareware
Scareware
Scareware is the type of malware that uses social engineering and fake warning messages. It will warn you that your computer is infected and will ask you to download a fake security program.
 Botnets
Botnets
A botnet (short for bot network) is a network of hijacked computers and devices infected with bot malware and remotely controlled by a hacker. The bot network is used to send spam and launch distributed denial of service (DDoS) attacks and may be rented out to other cybercriminals.
 Rootkits
Rootkits
A rootkit is a program (or collection of programs) that installs and executes code on a system without end-user consent or knowledge. It uses stealth to maintain a persistent and undetectable presence on the machine.
 Cryptominers
Cryptominers
Cryptominers are the type of malware that forces a computer to mine cryptocurrency for the attacker. The most common technique used by attackers is to use browser hijacking to infect computers.
How to know if you have a malware infection?
Here are some common symptoms of a device infected by malware:
- Annoying pop-ups that appear even if you don’t have your web browser open.
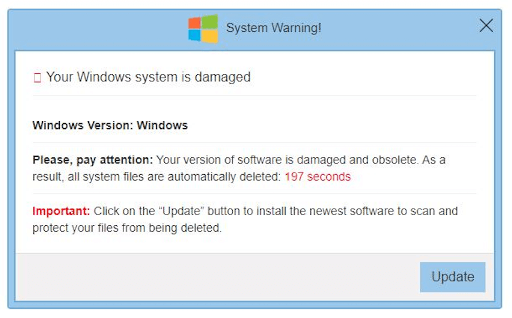
- Your internet browser shows inappropriate ads and multiple tabs regularly open suddenly.
- Unfamiliar toolbars or icons appear on your browser or desktop.
- When performing web searches, you get redirected to other sites.
- A different search engine appears when performing web searches.
- Suddenly your browser home page changes.
- Your desktop wallpaper was changed and contains a warning message.
- You see a scanning window from a fake antivirus program saying your PC is infected.
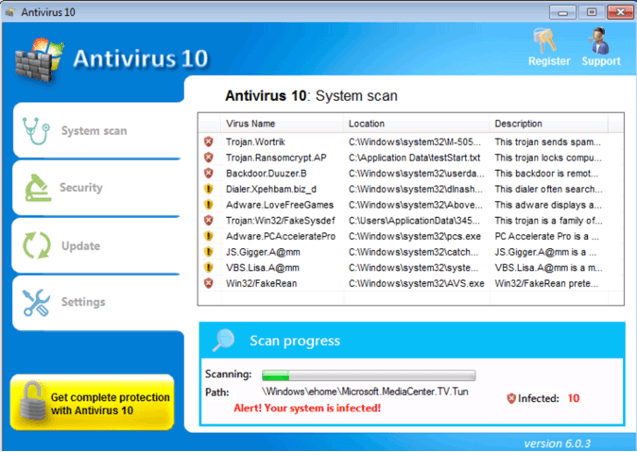
- Your computer suddenly slows down, some applications crash and you see random error messages.
- When you check the task manager, you see some strange processes running in the background potentially using an unusually large amount of processing power, even when you don’t have any programs open.
How malware gets on your device
Your device might get infected with malware through any of the following:
- Downloading free applications from unknown sources.
- Downloading movies, applications, or games using file-sharing applications or sites.
- inserting infected removable storage like external hard drives or thumb drives into your computer.
- clicking links embedded in fake warning messages or advertisements.
- entering your email address on suspicious account registration pages.
- opening email attachments from unknown senders.
How to remove malware
1. First things first, avoid using the infected machine for online banking, shopping, or other activities that require you to enter your private information like emails and passwords.
2. Make sure you have an antivirus program installed. We recommend that you download and install Trend Micro Premium Security Suite on your device. It offers complete multi-device protection against ransomware, viruses, dangerous websites, and identity thieves. It also has cloud-based AI technology that delivers highly effective and proactive protection against ever-evolving malware infections.
3. Update your security software. Getting the latest virus pattern updates will increase the chance of removing the malware infection.
4. Run a full malware scan on the infected device. Delete all files detected by your antivirus program. Sometimes a restart is needed to completely remove all the detected malicious files. You can run another scan after restarting to confirm that all the malicious files are removed.
8 tips to avoid malware
1. Download applications only from trusted sources. You can download them directly from the official website to avoid downloading from third-party hosting sites.
2. When installing an application, make sure you read all the prompts and watch out for notifications asking you to install additional add-ons or bundled applications. They might be dangerous and malicious.
3. Disable any internet browser add-ons that you are not using or are not familiar with. Sometimes, these add-ons are installed by suspicious programs and will steal information about your browsing habits.
4. When clicking a link in an email or on a website, you can hover your cursor over the link to see the actual URL where the link is going.
5. If you are not sure if a website or a link is safe, check the reputation of the site by copying the link and checking it on https://global.sitesafety.trendmicro.com/
6. When you see pop-up messages or ads, don’t click them. It’s almost always better to ignore them. Closing them will sometimes lead to other pop-ups suddenly opening.
7. Make a habit of scanning your USB drives and external drives before using them. This will ensure the device is safe to use and won’t infect other computers.
8. Install trusted antivirus software. Installing antivirus software greatly increases your defense against malware and will greatly decrease the chance of your device getting infected. You can download Trend Micro Maximum Security – it guards against cyberthreats with Web Threat Protection, Ransomware Protection, Anti-phishing, and Anti-spam Protection. Click the button below to give it a try:
