Trend Micro HouseCall for Home Networks: Giving You a Free Hand in Home Network Security
Remember when only desktop computers in our homes had connections to the internet? Thanks to the latest developments in smart device technology, almost everything now can be connected— security cameras, smart TVs, gaming consoles, and network storage, to name just a few. While a home network provides lots of benefits, it can also expose us to safety and privacy risks.
But checking for those risks need not be costly. How about a network security checker available for free? Yes, you read that right. Trend Micro’s free HouseCall for Home Networks (HCHN) scans the connected devices in your home network and detects those that pose security risks. And in doing so, it gives you a sense for what real network security entails. We have a solution for that also.
Want to know more?
Trend Micro HCHN uses intelligent network scanning technology to scan the devices connected to your home network for vulnerabilities. These can range from a low risk type—such as an easily identifiable Wi-Fi Name that hackers can use to attack your router and home network—to high risk types, such as SSL-Poodle (for man-in-the-middle attacks), Shellshock (for remote code execution attacks), Heartbleed (which puts website passwords at risk) and WannaCry (which is a Windows ransomware cryptoworm). These and other vulnerabilities can be detected through the help of this handy tool.
In addition, HCHN checks devices for open ports that are usually targeted by hackers and malware and can be exploited for cybercriminal activities. Examples include ports 20 and 21, used via the File Transfer Protocol (FTP) to transfer files between an FTP client (20) and FTP server (21), which can deliver a multitude of vulnerabilities to the internet; as well as port 23, which sends data in Clear Text, which can be used by attackers to listen in, watch for credentials, or inject commands, enabling the hacker to perform Remote Code Executions.
Moreover, HCHN gives you a report about the status of your home network and its connected devices and offers helpful advice for keeping your network and devices secure.
Lastly, HCHN provides you a notification when:
- A new device joins the network
- Connecting to a new network
- A new vulnerability is found in the network.
Ready to install?
HCHN is easy to use and accessible from any device, be it Windows (7, 8 and 10), macOS (10.12 or later), Android (5.0 or later) or iOS (8.0 or later). For your computer hardware, you just need to have Intel Pentium or compatible processor, a 256MB of RAM (512MB recommended) with at least 50MB available disk space and you’re set.
- Download and install the application from the Web, Google Play Store or Apple App Store.
- During install, accept the Privacy and Personal Data Collection Disclosure Agreement which indicates the necessary information gathered in order to check for and identify vulnerabilities in devices connected to your home network and you’re good to go.
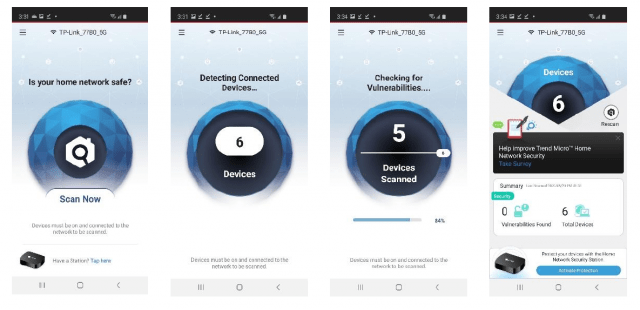
- Once installed, inspect your home network’s security risk exposure by clicking (applies to Windows and macOS) or tapping (applies to Android and iOS) Scan Now. You’re then presented with the result.
Are my home network and connected devices safe?
Here’s a few scans we did–from a Windows PC, then from and Android and iOS devices.
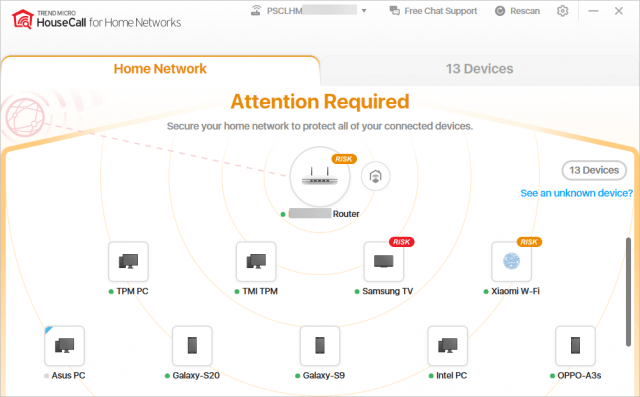
When the scan is complete on a Windows computer it shows two tabs: Home Network and Devices.
The first tab indicates a snapshot of your home network, identifying the devices at risk.
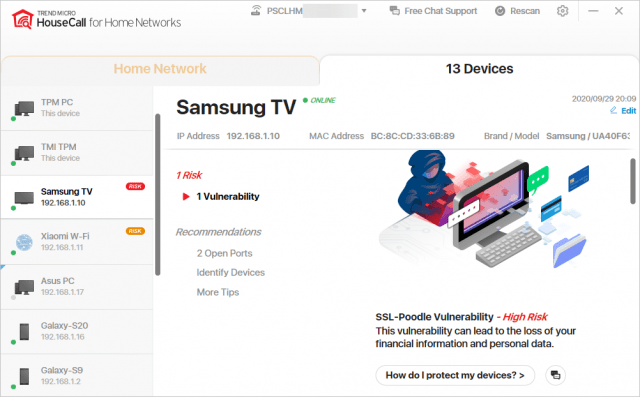
The second tab indicates a list of the devices scanned and the details of any device risks found.
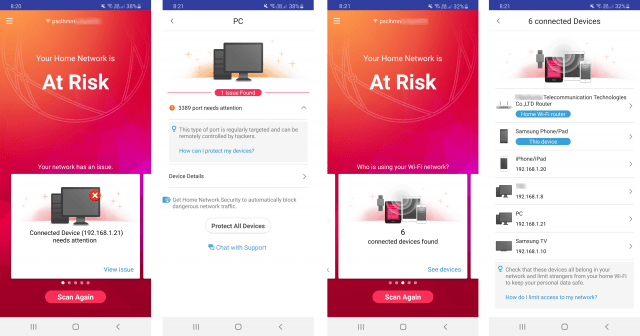
On the Android device, once the scan has finished, the screen will reveal any security risks detected. You can view the issue to see more details of the security risk in your home network. You can then slide to the next panel and check to verify all the connected devices on your network.
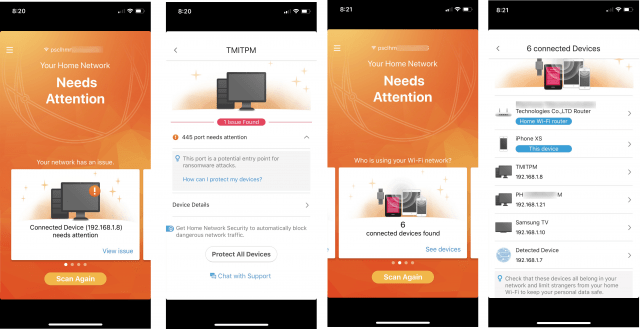
Similarly, upon completing the network scan from an iOS device, the app will display the risk that needs your attention. Just as with the Android device, you can move to the next panel to review the list of connected devices that were identified by Trend Micro HCHN.
A Few Reminders and Recommendations …
- Use HCHN regularly to check the posture of your home network security, since new vulnerabilities and network risks may appear in the device after a time due to lack of firmware updates or a failure by the manufacturer to address a newfound risk.
- Ensure that the devices (including mobile devices such as phones or tablets) are on and connected to the network when a scan is performed.
- Some security products installed from the device initiating the network scan might detect the scan as suspicious and show a warning message or block user access. This doesn’t mean that HCHN is a malicious application. Add HNCN to your security product’s exception list, so it’s allowed to examine your network and connected devices for security risks.
- The HNCN app does not automatically block dangerous network traffic or suspicious devices from connecting to your network. For that, and more home network security features, you should increase your home’s network protection with Trend Micro Home Network Security. To that we now turn.
What Home Network Security Provides
While a free network scan helps to determine the underlying dangers in your home network, to fully protect not only your home network but your family, you should consider Trend Micro Home Network Security (HNS) as a permanent enhancement to your network. It can shield your home against a wide variety of threats, including network intrusions, risky remote connections, phishing, ransomware, harmful websites and dangerous downloads. Additional features include the following:
- New Device Approval gives you control over the devices that are allowed access to your home network.
- Remote Access Protection limits malicious individuals from using remote desktop programs to connect to your devices at home.
- Voice Control lets you issue voice commands to Alexa or Google Home to perform specific functions on HNS such as conducting a scan, obtaining your home network’s security status, pausing internet usage, disabling internet access for a user, and so on.
- Parental Controls’ flexible and intuitive feature set, comprised of Filtering, Inappropriate App Used, Time Limits and Connection Alerts, can help any parent to provide a safe and secure internet experience for their kids. Combined with Trend Micro Guardian, parents can extend these protections to any network their children connect to, Wi-Fi or cellular.
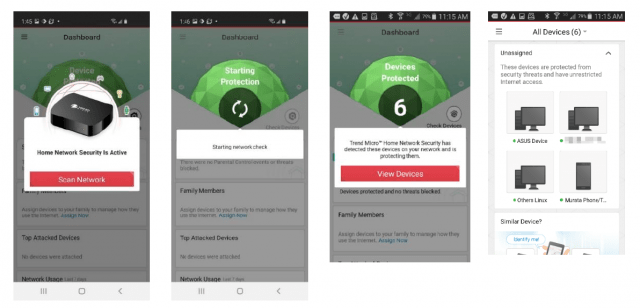
Download the Home Network SecurityApp on your Android or iOS device to give it a spin. Note that the HNS App, when used by itself, performs the same functions as the HCHN app on those devices.
If you like what you see, pair the HNS App to a Home Network Security Station to get the full range of protections. (Note too that once you do, the HCHN App will be disabled on all your devices and network and replaced by Home Network Security.)
Final Words
Home networks come with security risks. As the tech-savvy member of your household, you need to be aware of those risks. Using Trend Micro HouseCall for Home Networks (HCHN), you’ll be able to know which devices are connected to your home Wi-Fi network and whether these devices bear security risks that can be exploited by hackers and malicious software. Moreover, you’ll be provided with suggestions, in case your devices are found vulnerable.
However, just knowing the security risks is only half the battle in protecting your home network. You’ll need a more robust system that can automatically block suspicious and malicious traffic and do more— such as protecting your child’s online safety. Trend Micro Home Network Security (HNS) can address your home network’s security, even as it monitors your home network, prevents intrusions, blocks hacking attempts and web threats, and protects your family’s privacy, while keeping the internet safe for your kids.
Download Trend Micro HouseCall for Home Networks to give it a try, or go to Trend Micro Home Network Security to get more details on the solution, or to buy:
0 Comments
Other Topics
