Phishing scams targeting Meta users (including Facebook and Instagram) are on the rise. These scams often involve emails claiming to address security issues, tricking recipients into revealing sensitive information or accessing malicious links. Here’s how they work and what to watch out for.
How the Meta Security Scam Works
Cybercriminals orchestrate these phishing scams by crafting emails that appear to come directly from Meta, using official logos, branding, and language that closely resembles genuine Meta communications.
These messages often create a sense of urgency, warning users of “suspicious activity”, “account suspension”, or an “unauthorised log-in attempts”. By instilling fear, scammers prompt users to click on links that lead to fake log-in pages designed to mimic Meta’s official sites. Once victims enter their credentials, the scammers gain access to the users’ accounts, enabling them to steal personal information or take over the accounts entirely.
In a recent case, a would-be victim received the following very convincing phishing email, which purported to be from the Meta security team:
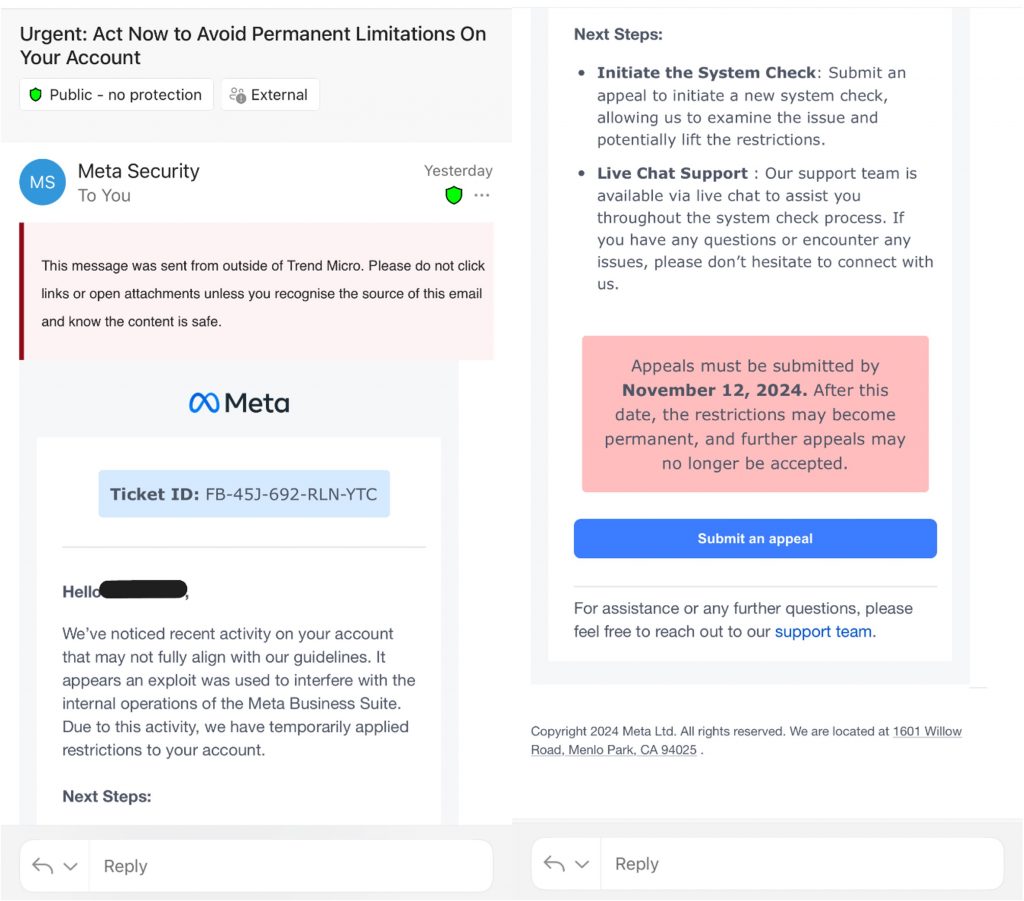
In this situation, the user has apparently been restricted due to inappropriate behavior. Note the high-pressure deadline: this is classic social engineering. To return to normal, the user must visit the “Meta” webpage and perform a so-called System / Security Check, as seen below:
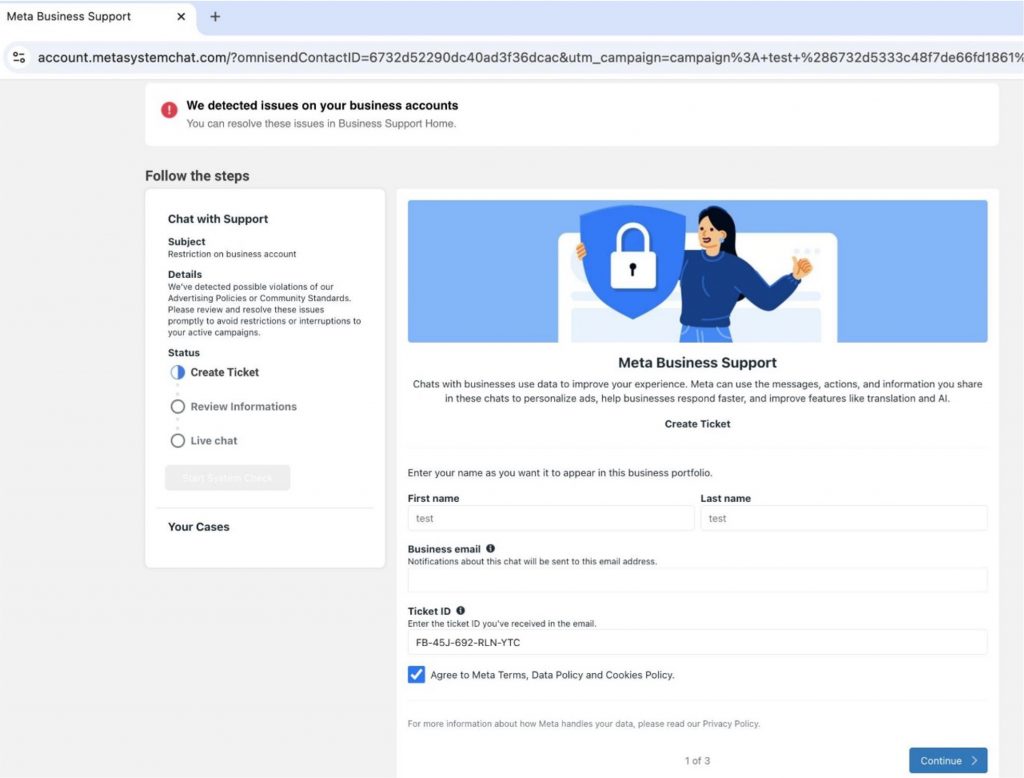
After creating the ticket, the victim is instructed to head over to their real Facebook account settings and acquire a two-factor authentication code. This code is what the scammers are really after — they can add this to the information they already have to comprehensively take over your account: don’t let them!
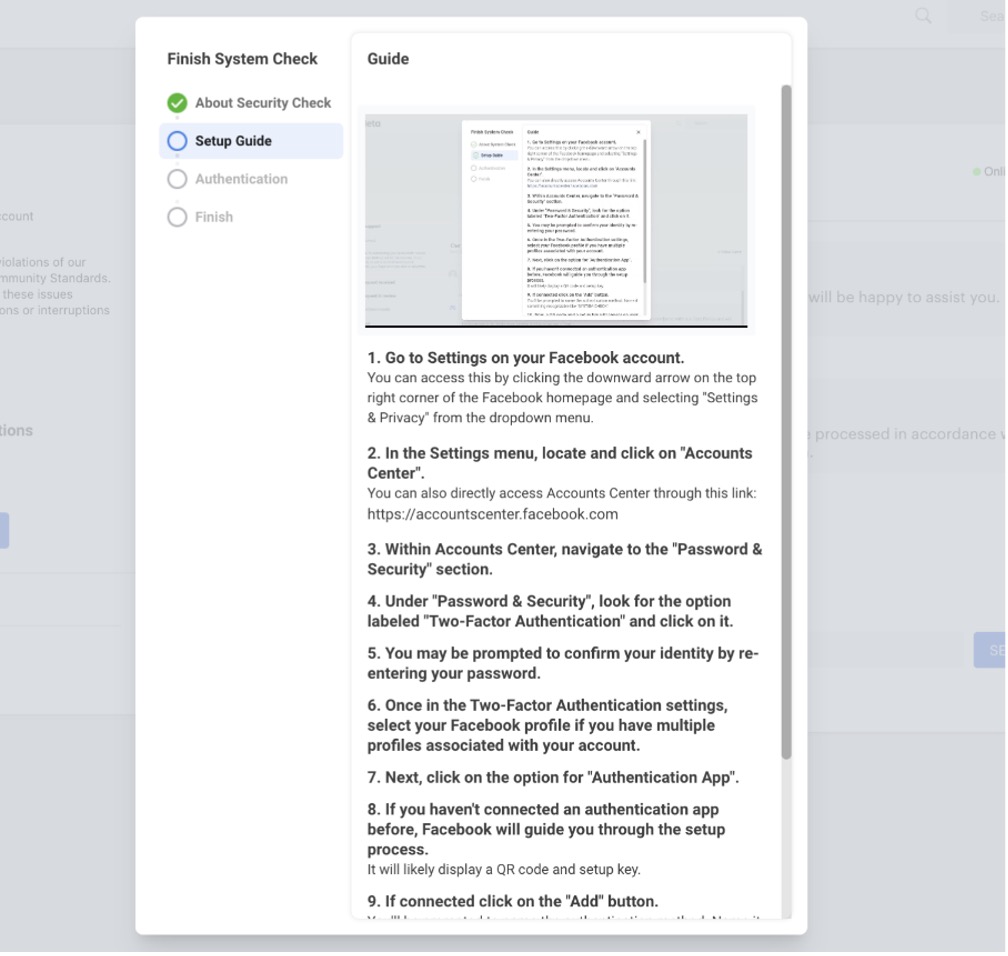
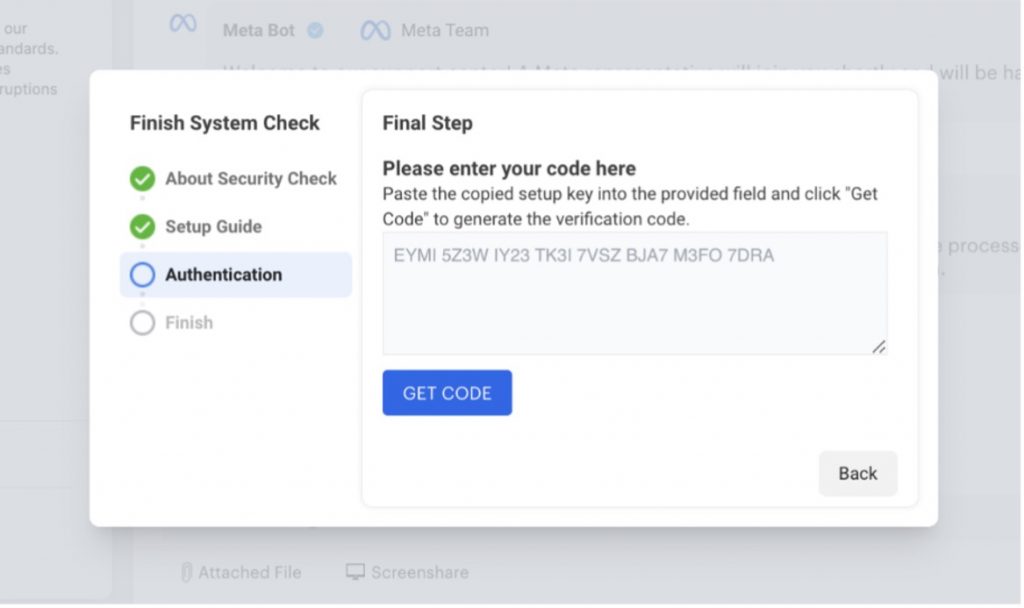
How to Spot a Phishing Email
- Sender’s Email Address: Always verify the sender’s email. Genuine Meta emails come from domains like @facebookmail.com or @instagram.com. The scam email above is: “noreply[at]salesforce[.]com”.
- Generic Salutations: Phrases like “Dear User” or “Account Holder” are red flags. Legitimate companies usually address users by name.
- Urgency or Fear Tactics: Claims that your account will be suspended immediately if you don’t act are a common trick.
- Suspicious Links: Hover over links to check the URL before clicking. Meta’s genuine URLs will always match their official domains. The scam URLs above are: “account[.]metasystemchat[.]com” and “krtra[.]com”.
- Grammatical Errors: Legitimate companies proofread communications. Typos or awkward phrasing are common in phishing emails.
What to Do If You Suspect a Phishing Attempt
- Do not click links: Avoid interacting with the email. Instead, log in to your account directly via the official website or app.
- Report it: Forward phishing emails to phish@facebook.com.
- Change your password: If you suspect your credentials were compromised, update your password immediately.
- Enable two- or multi-factor authentication (2FA): Adding an extra layer of security can help protect your account.
- Use Trend Micro ScamCheck! Available for both Android and iOS, it offers comprehensive protection from deceptive phishing scams, scam and spam text messages, deepfakes, and more.
