Phishing attacks continue to pose a significant threat in the ever-evolving cybersecurity landscape. Cybercriminals are employing increasingly sophisticated methods to deceive individuals and organizations, emphasizing the need for heightened vigilance and proactive defenses. Let’s delve into the top phishing statistics for 2024:
- Surge in Phishing Attacks
Phishing attacks grew by 58% last year, marking it as one of the fastest-growing cyber threats. Organizations must remain vigilant and adapt their security strategies accordingly. - Email Phishing Dominance
Email remains the most common vector for phishing attacks, accounting for a staggering 65% of all phishing attempts. Attackers are now crafting more convincing and realistic-looking emails to deceive recipients effectively. - Spear Phishing Targets High-Value Individuals
Spear phishing attacks, which are highly targeted and personalized, have risen by 30%. These attacks often focus on high-value individuals within organizations, such as executives and financial officers. Vigilance among leadership is crucial. - Escalating Phishing Success Rate
The success rate of phishing attacks has climbed to 18%, up from 14% last year. This alarming trend indicates that attackers are becoming more adept at bypassing security measures and manipulating victims. - Credential Theft Remains the Goal
An astonishing 70% of phishing attacks aim for credential theft. Cybercriminals seek unauthorized access to corporate networks and sensitive data, emphasizing the importance of robust authentication mechanisms. - Mobile Phishing on the Rise
Mobile phishing attacks have surged by 40%, exploiting vulnerabilities in mobile operating systems and applications. SMS phishing (smishing) and malicious apps pose significant risks to mobile users. - Financial Impact
Globally, the financial impact of phishing attacks has reached an estimated $3.5 billion in 2024. This includes both direct losses and the costs associated with remediation and recovery efforts. - Ransomware Links in Phishing Emails
Over 20% of phishing emails now contain links to ransomware. Attackers use these emails to deliver ransomware payloads, encrypting victims’ data and demanding ransoms for decryption keys. - Importance of Corporate Training and Awareness
Organizations that prioritize regular phishing awareness training for employees experience a remarkable 60% reduction in successful phishing attacks. Education remains a critical defense against phishing threats. - Dark Web Proliferation of Phishing Kits
The availability of phishing kits on the dark web has increased by 50%. These pre-packaged tools empower even novice cybercriminals to launch sophisticated phishing campaigns effortlessly. - Brand Impersonation Tactics
Brand impersonation in phishing emails is on the rise. Attackers frequently mimic well-known companies such as Microsoft, Amazon, and major banks, exploiting users’ trust in these familiar brands. - Government Impersonation
Phishing emails impersonating government agencies have seen a 35% increase. These deceptive messages often claim to be related to taxes, law enforcement, or pandemic-related relief programs. - AI-Driven Phishing
Artificial intelligence (AI) and machine learning play a role in creating more convincing phishing emails. AI-driven phishing can tailor messages to individual targets, increasing the likelihood of success. - Healthcare Sector Under Attack
The healthcare sector faces a 45% increase in phishing attacks, making it one of the most targeted industries. Cybercriminals seek to steal patient data or disrupt critical healthcare services. - User Vigilance Improving
Despite the rising threat, user vigilance is improving. Reports of suspected phishing emails by users have increased by 20%, reflecting growing awareness and proactive behavior.
Top Phishing Safety Tips
- Verify the Sender
Always check the sender’s email address carefully. Look for any discrepancies or unusual characters. If the email appears to be from a trusted organization but looks suspicious, contact the organization directly using a known phone number or email address. - Be Wary of Links and Attachments
Avoid clicking on links or downloading attachments from unknown or unexpected sources. Hover over links to see the actual URL before clicking, and only open attachments if you are certain they are safe. - Look for Red Flags
Phishing emails often contain spelling and grammatical errors, generic greetings (e.g., “Dear Customer”), and urgent or threatening language. Be skeptical of emails that create a sense of urgency or pressure you to act quickly. - Enable Two-Factor Authentication (2FA)
Enable 2FA on your online accounts whenever possible. This adds an extra layer of security by requiring a second form of verification, such as a text message or authentication app, in addition to your password. - Keep Software Updated
Ensure that your operating system, browser, and antivirus software are up-to-date. Security updates often include patches for vulnerabilities that phishers may exploit. - Educate Yourself and Others
Stay informed about the latest phishing techniques and educate those around you. Regular training and awareness programs can significantly reduce the risk of falling victim to phishing attacks. - Use Strong, Unique Passwords
Create strong passwords that are difficult to guess and use different passwords for each of your accounts. Consider using a password manager to help you keep track of your passwords securely. - Check for HTTPS
When entering sensitive information online, ensure that the website’s URL begins with “https://” and look for a padlock icon in the address bar. This indicates that the site uses encryption to protect your data. - Monitor Your Accounts Regularly
Regularly review your bank statements, credit card bills, and online account activity for any unauthorized transactions or changes. Report any suspicious activity to your financial institution immediately. - Report Phishing Attempts
Report phishing emails and websites to your email provider, IT department, or relevant authorities. Many email services have a “Report Phishing” option. By reporting phishing attempts, you can help prevent others from falling victim to the same attacks.
Protecting Your Identity and Personal Info
Compromised personal data can have serious consequences, including identity theft, financial fraud, and job losses. The best thing you can do is a) have reliable cybersecurity protection, and b) ensure you will find out ASAP in the event of being affected. We would encourage readers to head over to our new ID Protection portal, which has been designed to meet these challenges.
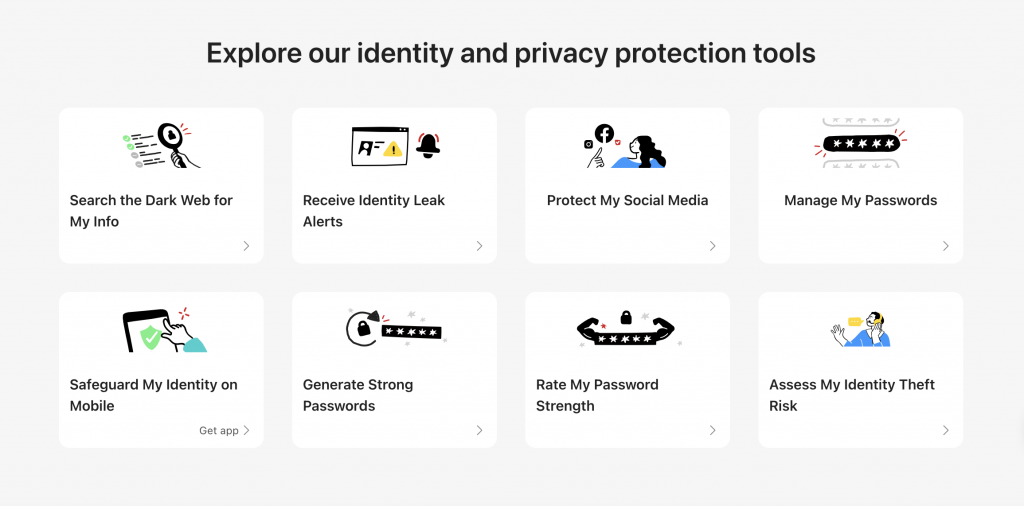
With ID Protection, you can:
- Check to see if your data (email, number, password, credit card) has been exposed in a leak, or is up for grabs on the dark web;
- Secure your social media accounts with our Social Media Account Monitoring tool, with which you’ll receive a personalized report;
- Create the strongest tough-to-hack password suggestions from our advanced AI (they’ll be safely stored in your Vault);
- Enjoy a safer browsing experience, as Trend Micro checks websites and prevents trackers.
- Receive comprehensive remediation and insurance services, with 24/7 support.
Offering both free and paid services, ID Protection will ensure you have the best safeguards in place, with 24/7 support available to you through one of the world’s leading cybersecurity companies. Trend Micro is trusted by 8 of the top 10 Fortune 500 Companies — and we’ll have your back, too.
Why not give it a go today? As always, we hope this article has been an interesting and/or useful read. If so, please do SHARE it with family and friends to help keep the online community secure and informed — and consider leaving a like or comment below. Here’s to a secure 2024!
0 Comments
Other Topics
