In today’s digital age, staying connected on our mobile devices has become a way of life. But what happens when our devices run out of juice while we’re out and about? We often rely on public charging stations to power up our devices quickly, but did you know that these stations could be a gateway for cybercriminals to access your personal data?
What Is Juice Jacking?
Juice jacking is a type of cyber-attack where an attacker steals data from a mobile device or installs malware on it using a public USB charging port. It is a growing concern for mobile device users everywhere.
How Does Juice Jacking Work?
Attackers can use various techniques, such as:
- Malicious charging cables — These are designed to look like legitimate charging cables, but are actually modified to include extra components that allow the attacker to gain access to the device.
- Modified USB ports — This could involve installing a small device, known as a “juice jacking adapter”, that intercepts the data being transferred between the device and charging port.
What’s the Risk and Should I Be Worried?
Public charging stations are often unsecured and can be easily compromised by attackers. Juice jacking attacks can occur in various locations, including:
- Airports
- Hotels
- Charging kiosks
- Coffee shops
- Train stations

Attackers may even create entirely fake charging stations. Frequent use of public charging stations increases the risk of juice jacking attacks, making it essential to take steps to protect yourself from these threats. Juice jacking attacks can take various forms, but the most common types are:
- Data theft — Attackers steal your personal or financial information.
- Malware installation — Attackers install malicious software on your device that can compromise its security or steal your data.
- Man-in-the-middle attacks — Attackers intercept your device’s communication with the charging station, and can access your data or modify it, before forwarding it to the intended recipient.
How Do I Know if a Public Charging Station Is Safe to Use?
It can be difficult to know if a charging station will juice jack you. However, some signs that a charging station might be compromised include:
- The absence of branding or the presence of an unusual logo on the charging station
- If the charging station requires you to install software or enter personal information
- Your device running slower than usual
- Unexpected pop-ups on your device
- Strange apps or files on your device
- Increased data usage
If you notice any of these signs, it’s best to avoid using the charging station.
Top Tips for Charging Your Mobile Device in Public
- Always use your own charging equipment to avoid juice jacking attacks.
- Use a charging-only cable. Some USB cables are designed for charging only and do not have data transfer capabilities.
- Consider using a wall charger instead of a USB port to charge your device.
- Use a portable battery charger to avoid using public charging stations.
- Use USB Data Blockers, also known as “USB condoms”, to prevent data transfer.
- Enable your device’s own security settings.
- Protect your device from security vulnerabilities by keeping it up to date with the latest security patches.
- Use antivirus software like Trend Micro Mobile Security, which will give you the defense you need against malicious apps and malware that can be installed during juice jacking.
Protecting Your Identity and Personal Info
Compromised credentials can have serious consequences, including identity theft and financial fraud. The best thing you can do is a) have reliable cybersecurity protection, and b) ensure you will find out ASAP in the event of being affected. We would encourage readers to head over to our new FREE ID Protection platform, which has been designed to meet these challenges.
With ID Protection, you can:
- Check to see if your data (email, number, password, social media) has been exposed in a leak,
- Secure your social media accounts with our Social Media Account Monitoring tool, with which you’ll receive a personal report,
- Receive the strongest tough-to-hack password suggestions from our advanced AI.
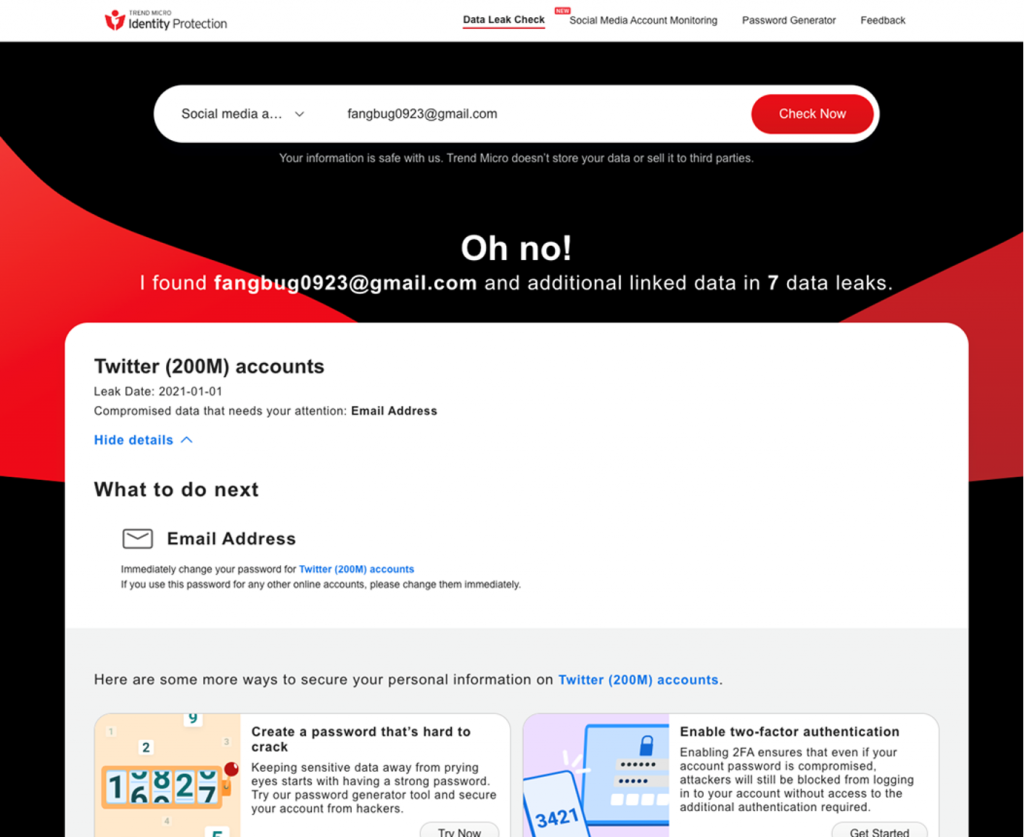
All this for free — give it a go today. As always, we hope this article has been an interesting and/or useful read. If so, please do SHARE it with family and friends to help keep the online community secure and informed — and consider leaving a like or comment below. Here’s to a secure 2023!
