Log4j Bug: The Worst Cyberthreat in a Decade, Affecting Google, Apple, Amazon, Netflix and More!
What Is log4j & Why Does It Matter?
“Log4Shell” is the name of the bug recently discovered in the Java “log4j” tool. It is being regarded by many as the worst hack ever encountered.
The internet is on fire right now, figuratively speaking. In addition, it has been claimed that in the 12 hours following the bug’s existence being reported, it had already been fully weaponized by cybercriminals. Amit Yoran of Tenable, called it “the single biggest, most critical vulnerability of the last decade”. Log4Shell has also been rated 10/10 by the Apache Software Foundation in its threat score.
Experts are urging companies to patch up immediately — the problem being “That could take hours, days or even months depending on the organization,” said Jon Clay, vice president of threat intelligence here at Trend Micro.
Are Hackers Exploiting It?
Log4Shell grants criminals and spies easy access to internal networks where they can steal data, plant malware and erase information. Because almost every company uses Java, everyone is at risk.
“I’d be hard-pressed to think of a company that’s not at risk,” said Joe Sullivan of Cloudflare. The truth is that millions of servers have it installed. Those proven to be vulnerable include: Google, Amazon, Netflix, Android, Apple, IBM, Tesla, Badu, Twitter, Steam, Alibaba, and Minecraft (where the bug was first encountered).
Anyone with the bug know-how can obtain full access to a computer that uses the same Java software. It is as simple as copying, pasting, and sending some code text in a message. It was users on Minecraft who first illustrated Log4Shell’s capability. Users were found to be taking control of rivals’ computers with the bug by simply pasting a short code message in the chatbox.
60 mutant strains have been detected — causing grave concern for the future. Experts have stated that it could be “months if not years” before the bug is effectively countered.
How to Protect Yourself from the Log4Shell Security Flaw
With a security incident this big, it’s better to expect the worst. The bug can also influence your home network and your NAs storage. Furthermore, personal information like email addresses, credit card info and the like can be disclosed in data breaches resulting from this vulnerability. Here are some recommendations that can help protect your devices and applications from this vulnerability:
1. Update your applications (patched to the latest version)
Affected applications like Minecraft have already released a patch for this vulnerability. You should expect other services and applications to do the same — so make sure you always check for the latest updates.
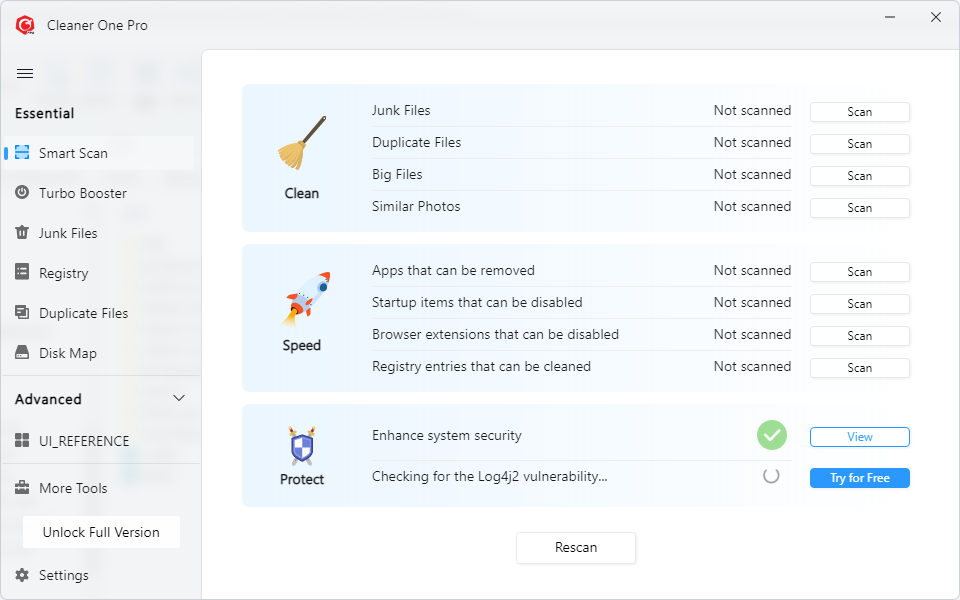
2. Check if your computer is safe
Scan and check if your device is vulnerable to log4shell security flaw for free with Cleaner One Pro
3. Scan devices on your home network
Trend Micro’s HouseCall for Home Networks is a very good, free scan & fix product. It guards against and cleans up cyber threats, including viruses, worms, Trojans, and spyware. A home network scanner will go some distance in protecting yourself from security flaws of this type.
4. Install a trusted antivirus program
Trend Micro Maximum Security can detect the exploit attempts from this vulnerability. Trend Micro Web Reputation Services (WRS) has blocked malicious reporting and communication vectors associated with the observed exploits.
4. Use ID Security to protect your personal information
Trend Micro ID Security scours the dark web for any mention of your data (SSN, email addresses, passwords, codes etc.) in the event of it being sold or maliciously shared by cybercriminals.
0 Comments
Other Topics
