It’s estimated that there are 30 million Facebook accounts belonging to deceased persons today. One study from the University of Oxford estimated that by 2100 this figure could be as high as 4.9 billion — with 1.4 billion as a minimum.
With contemporary life intertwined with the internet, most of us now have large digital footprints online — to put it simply, information about us is everywhere. The question is what happens to this information when we die or become incapacitated?
What is a Digital Legacy?
A digital legacy is the bread crumb trail of our online life, once we’re no longer active through death or illness. It includes all the things we’ve done on the internet: for example, emails, social media accounts, photos, documents, shopping accounts, and administrative and healthcare accounts. In essence, it’s all the digital acts we perform in life.
When we’re no longer around, our digital legacy nonetheless remains, and it’s important to think about who should take care of it and what should happen to it. Some people write down instructions for their digital legacy in their wills, or use special tools to decide who gets access to it after they’re gone.
Why Is a Digital Legacy Important?
There are many things to consider when it comes to a digital legacy plan:
- Preserving Memoirs
- Having an archive of treasured moments like pictures, videos, and messages shared on different social media platforms.
- Healing and Closure
- This can provide comfort and facilitate the grieving process. Sharing photos can help in coping with the loss.
- Legal and Financial Considerations
- Online digital assets such as online bank accounts, insurance, and cryptocurrencies have financial value. There’s a need to ensure assets are managed correctly.
- Honoring Wishes
- Some people have certain wishes for how to handle their accounts and these should be honored.
- Genealogy and Family Lineage
- Organizing this can provide insights into family history and genealogy for later generations. With this information you can track down family relationships, relatives, and connections.
- Research and Educational Purposes
- Protecting and managing information can provide insights into social trends, current events, cultural practices and more. This will be beneficial for research and education.
- Identity Protection
- Unmanaged, dormant online accounts are susceptible to hacking and misuse, and can be used to commit identity theft and fraud.
What Are the Risks?
With the centrality of a digital legacy to a person’s life, there are a multitude of risks arising from no, or poor, management:
- Negative Legacy
- Embarrassing content left behind in digital form can tarnish the deceased person’s reputation. It could negatively impact how they are remembered by others.
- Emotional Distress
- Unwanted access to a deceased person’s online accounts and messages could cause great distress to family members and friends.
- Loss of Digital Assets
- Assets such as photos, documents, and videos, may get lost if they are not stored and preserved properly.
- Legal Complications
- Unresolved digital assets can cause legal complications, while mismanaged financial matters can create conflict within the family.
- Misuse of Account
- Without instructions, someone might misuse the departed person’s account.
- Privacy Breaches
- Without security management, personal information can be exposed to hackers or strangers, and will be sold on the black market.
- Identity Theft
- Malicious actors can use a deceased person’s identity for things such as loan applications, and fraudulent bank accounts.
How to Deal with Digital Legacies
Now that we know the importance of digital legacies, let’s look at the current protocols of some large online companies. Configuring our online accounts will ensure that our accounts will be deleted or passed on to trusted people who can handle our information responsibly.
- Google (Gmail, Drive, and more)
- Go to your Google Account settings.
- Look for “Data & personalization”.
- Under “Download, delete, or make a plan for your data”, click on “Make a plan for your account”.
- Follow the instructions to set up your inactive account manager. You can choose up to 10 contacts to be notified, or for data to be deleted after a period of inactivity.
- Apple (for iPhone users)
- Navigate to your iPhone’s settings.
- Tap on your Apple ID.
- Tap on “Password & Security”.
- Under “Legacy Contact”, tap on “Add Legacy Contact” and follow the instructions to select a contact from your address book.
- Facebook
- Go to your Facebook settings.
- In the left column, click on “Memorialization Settings”.
- Locate “Choose a friend” and click “Edit”.
- Select the friend you want to be your legacy contact.
- You can also choose whether to allow your legacy contact to download an archive of your posts and profile information.
- Microsoft
- Go to your Microsoft Account settings.
- Look for “Security & privacy”.
- Under “Your info”, select “Manage how your Microsoft account is managed after you die”.
- Follow the instructions to set up your legacy contacts and specify what you want them to be able to do with your account.
Protecting Your Identity and Personal Info
Trend Micro is here to have your back in 2024. We would encourage readers to head over to our new ID Protection platform, which has been designed to meet the security and privacy threats we now all face.
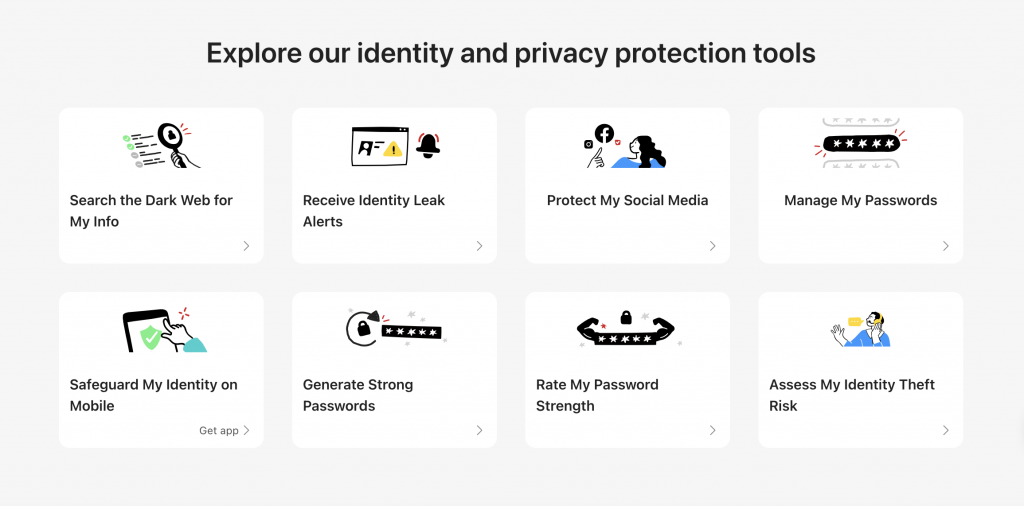
With ID Protection, you can:
- Check to see if your data (email, number, password, credit card) has been exposed in a leak, or is up for grabs on the dark web;
- Secure your social media accounts with our Social Media Account Monitoring tool, with which you’ll receive a personalized report;
- Create the strongest tough-to-hack password suggestions from our advanced AI (they’ll be safely stored in your Vault);
- Enjoy a safer browsing experience, as Trend Micro checks websites and prevents trackers.
- Receive comprehensive remediation and insurance services, with 24/7 support.
Offering both free and paid services, ID Protection will ensure you have the best safeguards in place, with 24/7 support available to you through one of the world’s leading cybersecurity companies. Trend Micro is trusted by 8 of the top 10 Fortune 500 Companies — and we’ll have your back, too.
Why not give it a go today? As always, we hope this article has been an interesting and/or useful read. If so, please do SHARE it with family and friends to help keep the online community secure and informed — and consider leaving a like or comment below. Here’s to a secure 2024!
